Category: Red Teaming - Tools - Recon-ng
The more you know about your target’s infrastructure and personnel, the better you can orchestrate your attacks.
Reconnaissance (recon) can be defined as a preliminary survey or observation of your target (client) without alerting them to your activities. If your recon activities create too much noise, the other party would be alerted, which might decrease the likelihood of your success.
Some specific objectives by Reconnaissance:
- Discovering subdomains related to our target company
- Gathering publicly available information about a host and IP addresses
- Finding email addresses related to the target
- Discovering login credentials and leaked passwords
- Locating leaked documents and spreadsheets
Reconnaissance can be broken down into two parts:
- Passive reconnaissance: can be carried out by watching passively
- Active reconnaissance: requires interacting with the target to provoke it in order to observe its response.
In this lab, we will be focusing on passive reconnaissance, i.e., techniques that don’t alert the target or create ‘noise’.
Recon-ng
🚩Recon-ng is a framework that helps automate the OSINT work. It uses modules from various authors and provides a multitude of functionality. Some modules require keys to work; the key allows the module to query the related online API.
Recon-ng can be used to find various bits and pieces of information that can aid in an operation or OSINT task. All the data collected is automatically saved in the database related to your workspace.For instance, you might discover host addresses to later port-scan or collect contact email addresses for phishing attacks.
At this stage, you need to select the installed module you want to use. However, if this is the first time you’re running recon-ng, you will need to install the module(s) you need.
- To run the programs as a
rootusertypesudo suand press Enter
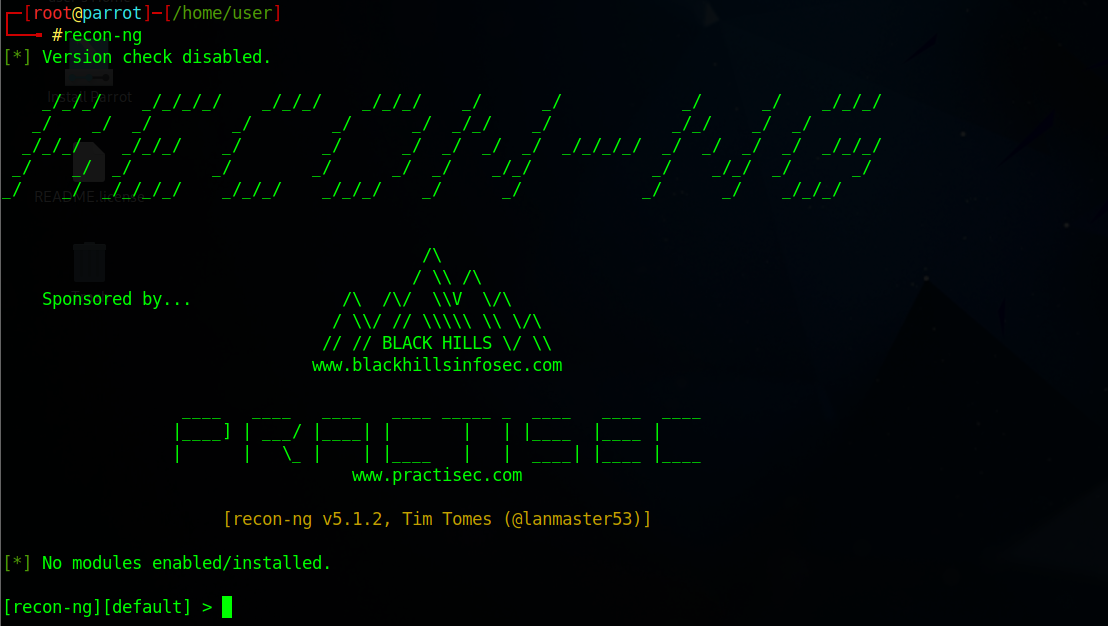
- You can start Recon-ng by running the command
recon-ng. Starting Recon-ng will give you a prompt like[recon-ng][default] >.
- Type
helpto view all the commands that allow you to add/delete records to a database, query a database, etc.
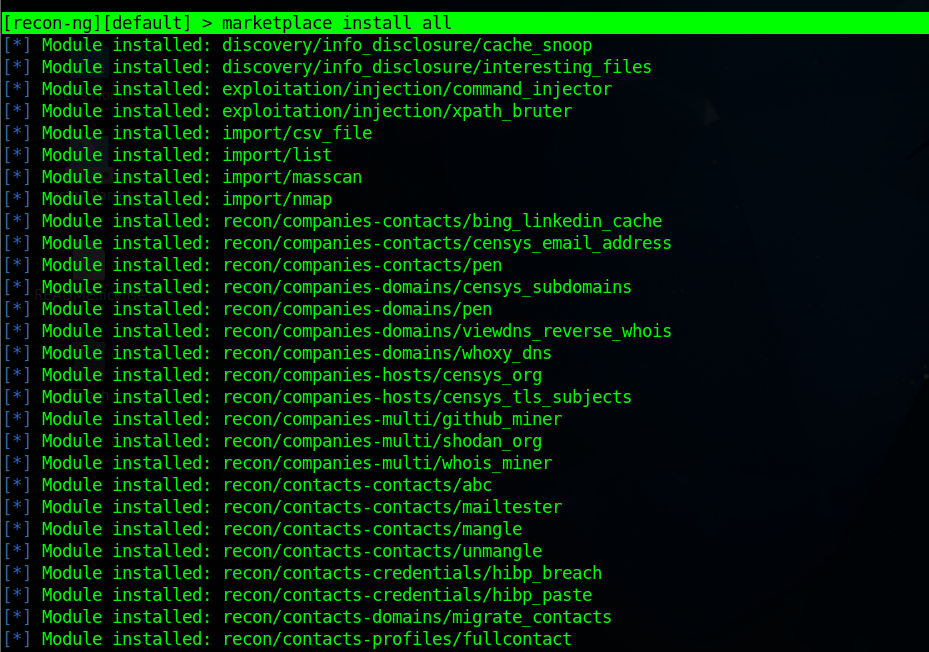
-
💡 If this is the first time you’re running
recon-ng, you will need to install the module(s) you need.[recon-ng][default] > marketplace install all
-
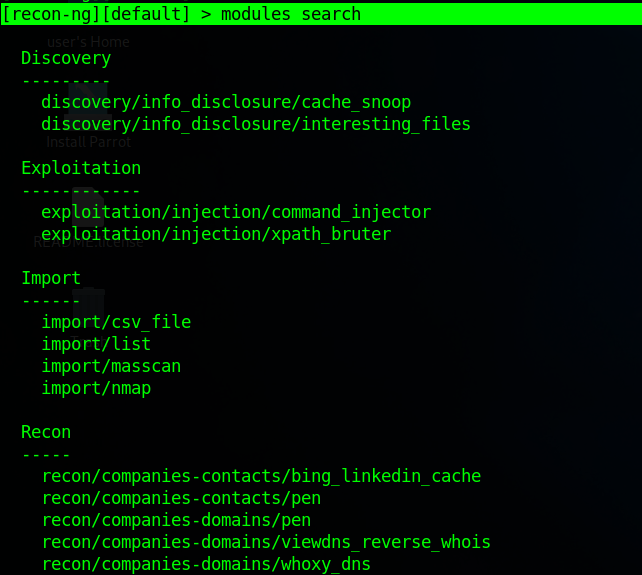
💡 To displays all the modules available in recon-ng:
[recon-ng][default] > modules search
▶️ Steps:
- Create a workspace for your project
- Insert the starting information into the database
- Search the marketplace for a module and learn about it before installing
- List the installed modules and load one
- Run the loaded module
Creating a Workspace
- Create a workspace in which to perform network reconnaissance named CEH
-
Run
workspaces create WORKSPACE_NAMEto create a new workspace for your investigation.For example,
workspaces create CEHwill create a workspace namedCEH
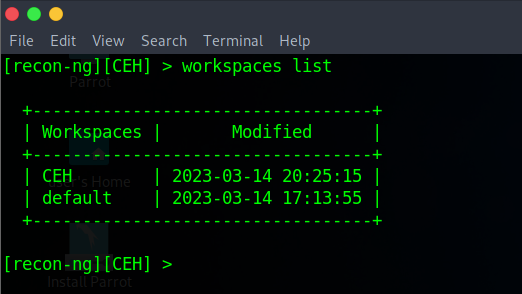
▶️ To displays a list of workspaces type:
[recon-ng][CEH] > **workspaces list
Seeding the Database
In reconnaissance, you are starting with one piece of information and transforming it into new pieces of information. For instance, you might start your research with a company name and use that to discover the domain name(s), contacts and profiles.
Then you would use the new information you obtained to transform it further and learn more about your target.
-
Add a domain in which you want to perform network reconnaissance
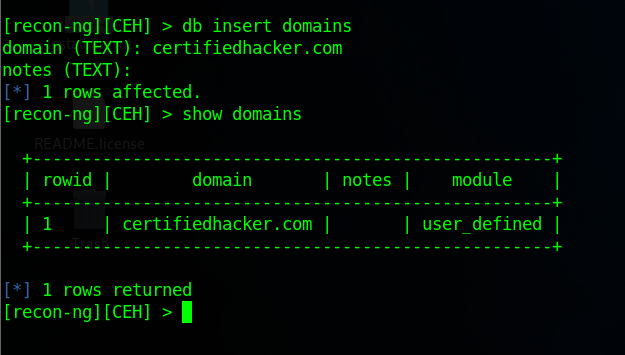
Run
db insert domainsand press Enteradd domain name:
certifiedhacker.com▶️ To displays a list of domains:
show domains
Harvest the hosts-related information associated with certifiedhacker.com by loading network reconnaissance modules such as:
- brute_hosts
- Netcraft
- Bing
| Module | Path |
|---|---|
| brute_hosts | recon/domains-hosts/brute_hosts |
| Netcraft | recon/domains-hosts/netcraft |
| Bing | recon/domains-hosts/bing_domain_web |
-
To load the recon/domains-hosts/brute_hosts module, type the
modules load recon/domains-hosts/brute_hostscommand and press Enter.Result:
[recon-ng][CEH] > modules load recon/domains-hosts/brute_hosts [recon-ng][CEH][brute_hosts] > run ------------------- CERTIFIEDHACKER.COM ------------------- [*] No Wildcard DNS entry found. [*] 1.certifiedhacker.com => No record found. [*] 02.certifiedhacker.com => No record found. [*] 10.certifiedhacker.com => No record found. [*] 13.certifiedhacker.com => No record found. [*] 14.certifiedhacker.com => No record found. [*] 11.certifiedhacker.com => No record found. [*] 12.certifiedhacker.com => No record found. ... [*] www.certifiedhacker.com => (A) 162.241.216.11 [*] Country: None [*] Host: www.certifiedhacker.com [*] Ip_Address: 162.241.216.11 [*] Latitude: None [*] Longitude: None [*] Notes: None [*] Region: None [*] -------------------------------------------------- ... ------- SUMMARY ------- [*] 22 total (19 new) hosts found.▶️ To displays a list of hosts
show hosts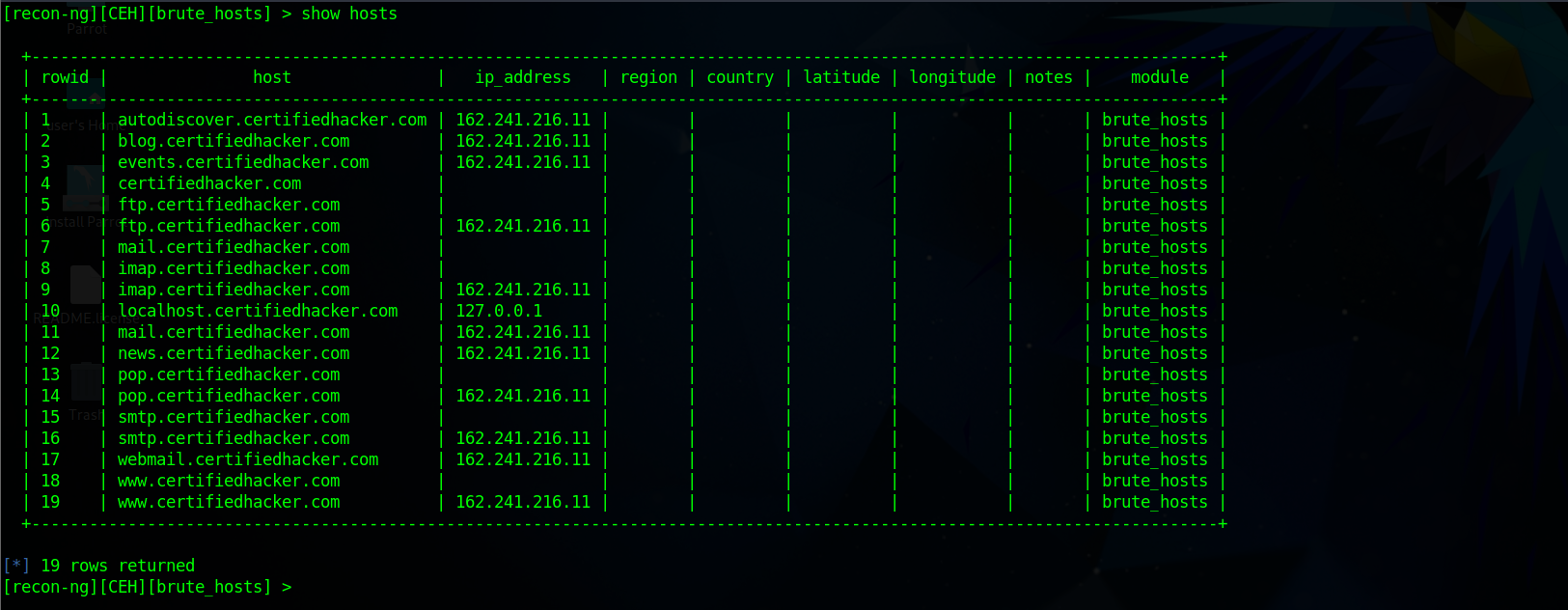
-
To load the recon/domains-hosts/bing_domain_web module, type the
modules load recon/domains-hosts/bing_domain_webcommand and press Enter.Result:
[recon-ng][CEH] > modules load recon/domains-hosts/bing_domain_web [recon-ng][CEH][bing_domain_web] > run ------------------- CERTIFIEDHACKER.COM ------------------- [*] URL: https://www.bing.com/search?first=0&q=domain%3Acertifiedhacker.com [*] Country: None [*] Host: webmail.certifiedhacker.com [*] Ip_Address: None [*] Latitude: None [*] Longitude: None [*] Notes: None [*] Region: None [*] -------------------------------------------------- [*] Country: None [*] Host: www.certifiedhacker.com [*] Ip_Address: None [*] Latitude: None [*] Longitude: None [*] Notes: None [*] Region: None [*] -------------------------------------------------- [*] Sleeping to avoid lockout... [*] URL: https://www.bing.com/search?first=0&q=domain%3Acertifiedhacker.com+-domain%3Awebmail.certifiedhacker.com+-domain%3Awww.certifiedhacker.com ------- SUMMARY ------- [*] 2 total (0 new) hosts found.**▶️ To displays a list of hosts
show hosts
c. To load recon/hosts-hosts/reverse_resolve module, type the
modules load recon/hosts-hosts/reverse_resolvecommand and press Enter.Result:
[recon-ng][CEH] > modules load recon/hosts-hosts/reverse_resolve [recon-ng][CEH][reverse_resolve] > run [*] Country: None [*] Host: box5331.bluehost.com [*] Ip_Address: 162.241.216.11 [*] Latitude: None [*] Longitude: None [*] Notes: None [*] Region: None [*] -------------------------------------------------- [*] 127.0.0.1 => No record found. ------- SUMMARY ------- [*] 1 total (1 new) hosts found.▶️ New record added by module:
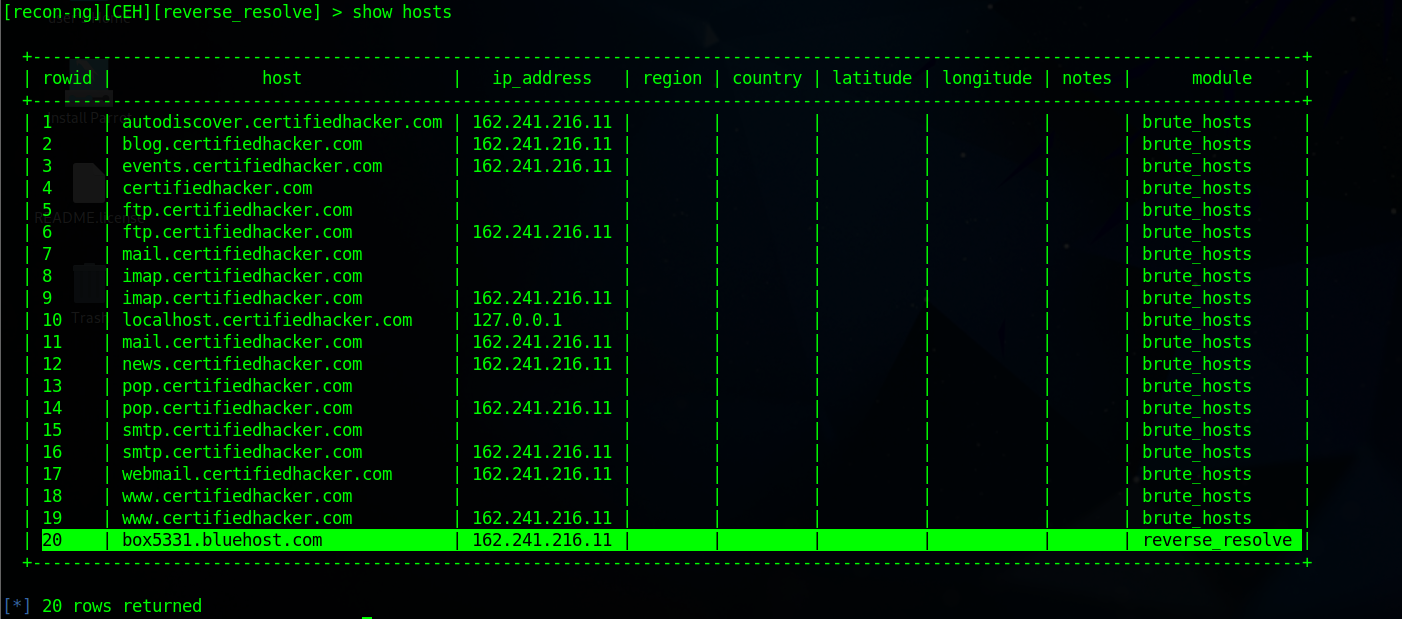
Reporting
There are many type of reporting like:
[recon-ng][CEH] > modules search report
[*] Searching installed modules for 'report'...
Reporting
---------
reporting/csv
**reporting/html**
reporting/json
reporting/list
reporting/proxifier
reporting/pushpin
reporting/xlsx
reporting/xml
Type the modules load reporting command and press Enter
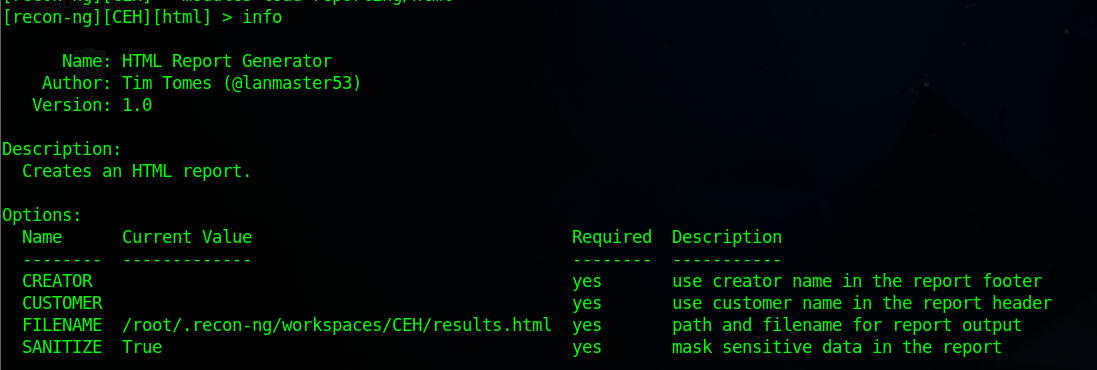
use [recon-ng][CEH] > modules load reporting/html
you need to assign values for CREATOR and CUSTOMER options while the FILENAME value is already set, and you may change the value if required.
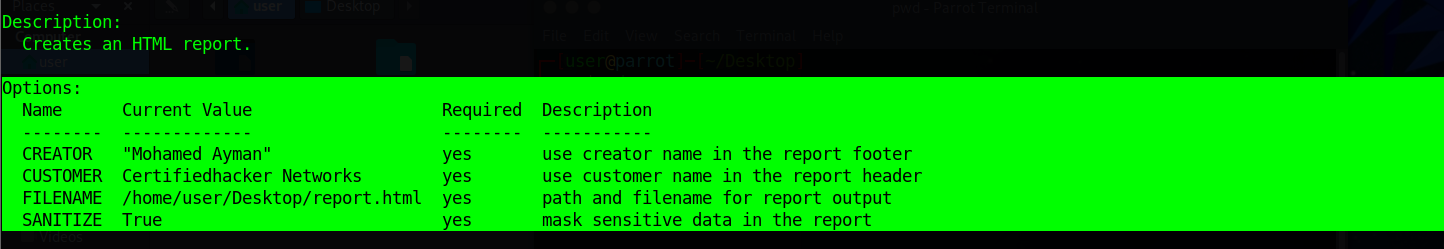
Type:
options set FILENAME /home/attacker/Desktop/results.htmland press Enter. By issuing this command, you are setting the report name as results.html and the path to store the file as Desktop.options set CREATOR [your name]and press Enter.options set CUSTOMER Certifiedhacker Networks(since you have performed network reconnaissance on certifiedhacker.com domain} and press Enter.
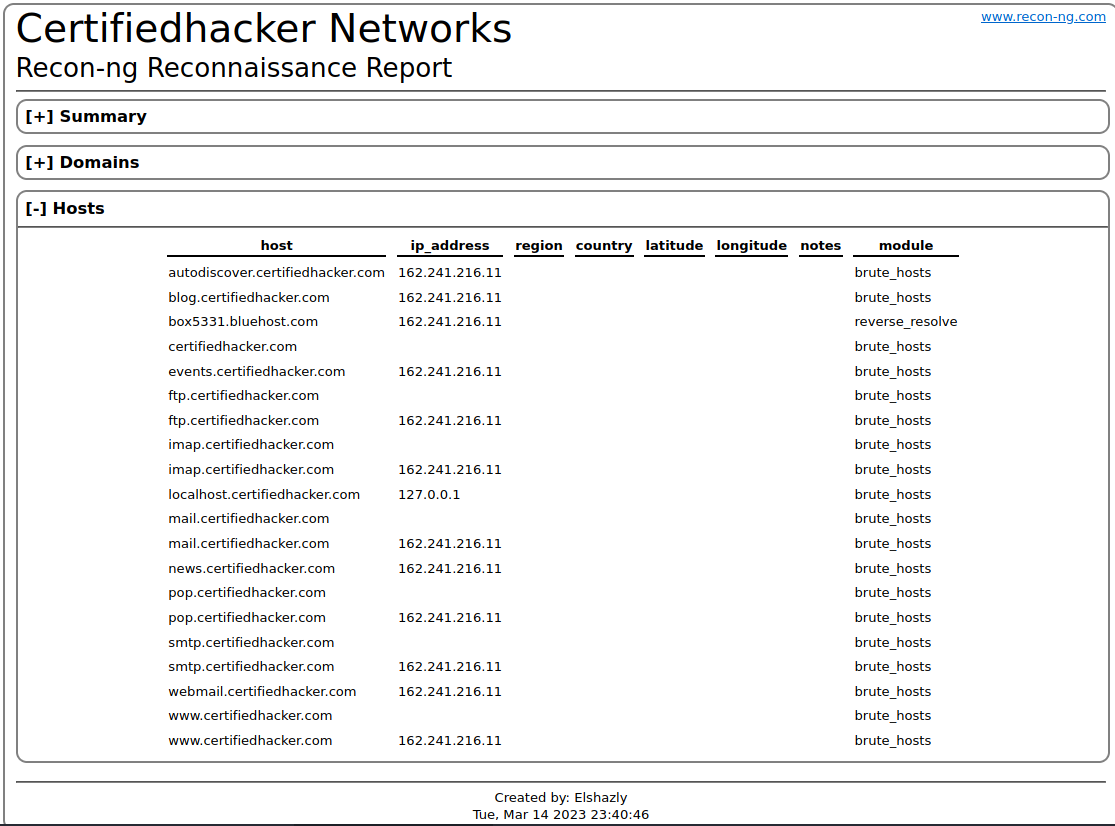
▶️ HTML Report:
💡Now, we will use Recon-ng to gather personnel information.
- run
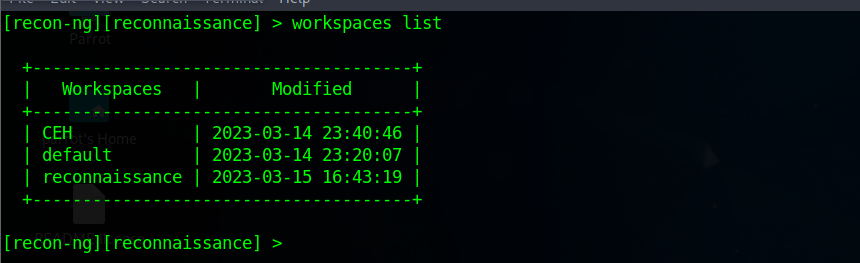
recon-ngand create new workspaces calledreconnaissance
- run
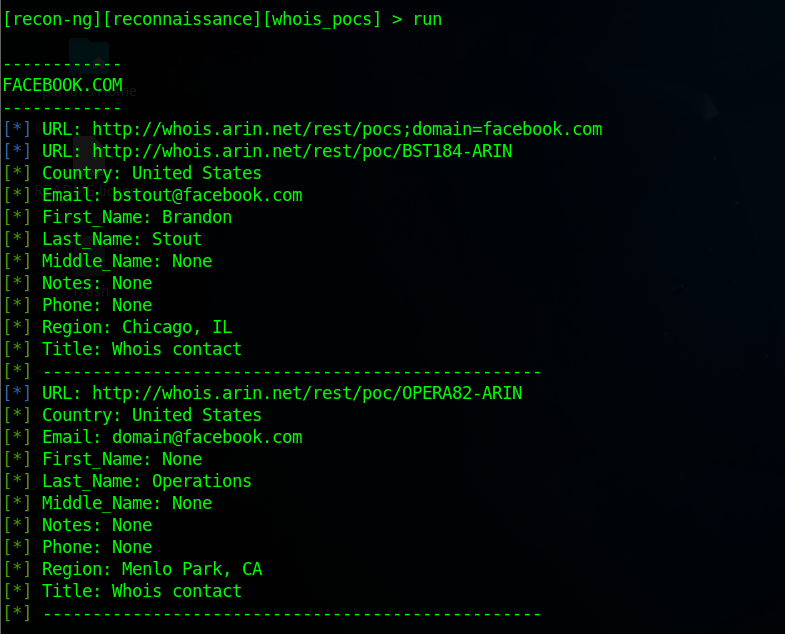
modules load recon/domains-contacts/whois_pocs
-
run
show contacts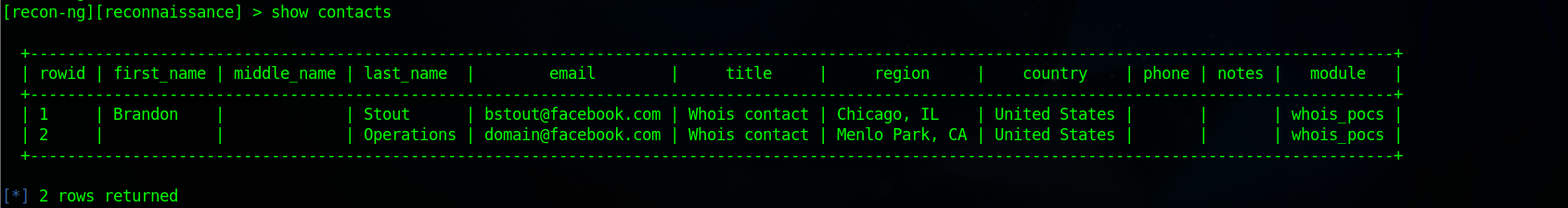
Now, we will validate the existence of names (usernames) on specific websites.
run modules load recon/profiles-profiles/namechk
show the result of profile command :
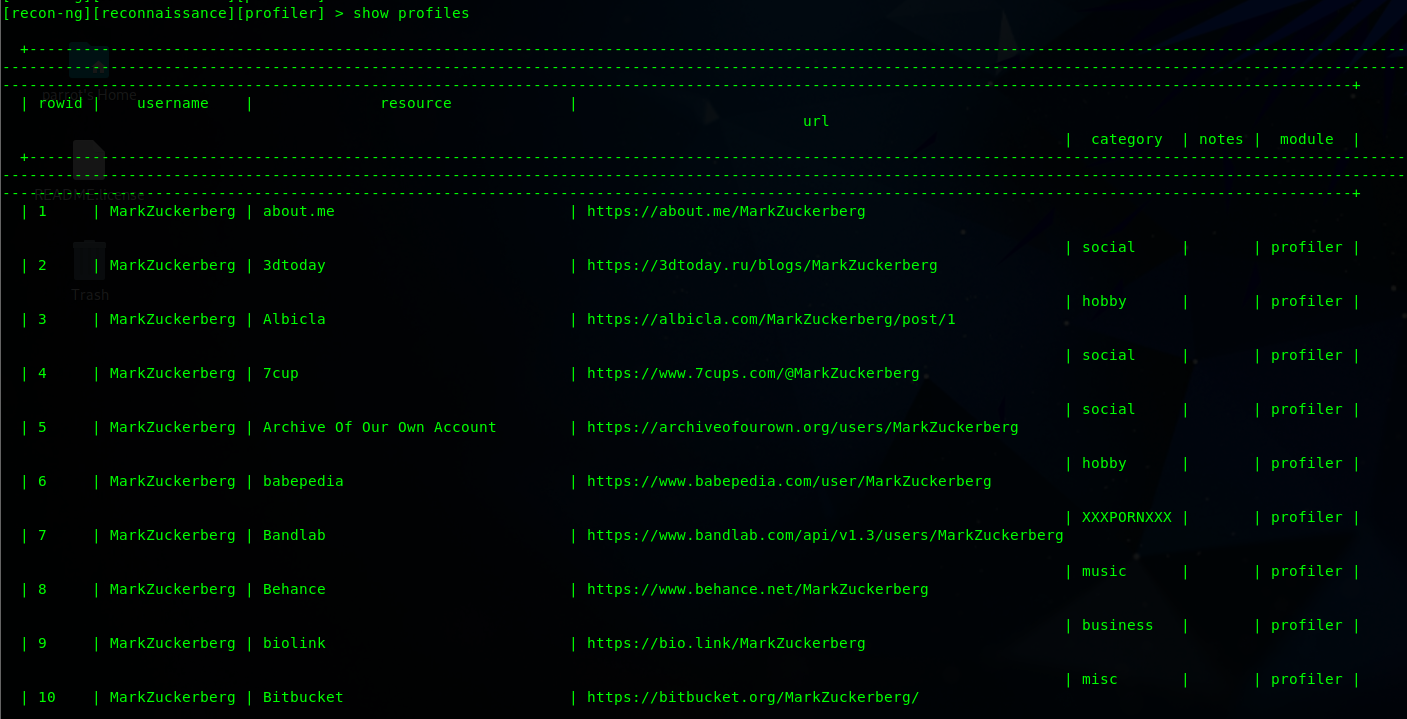
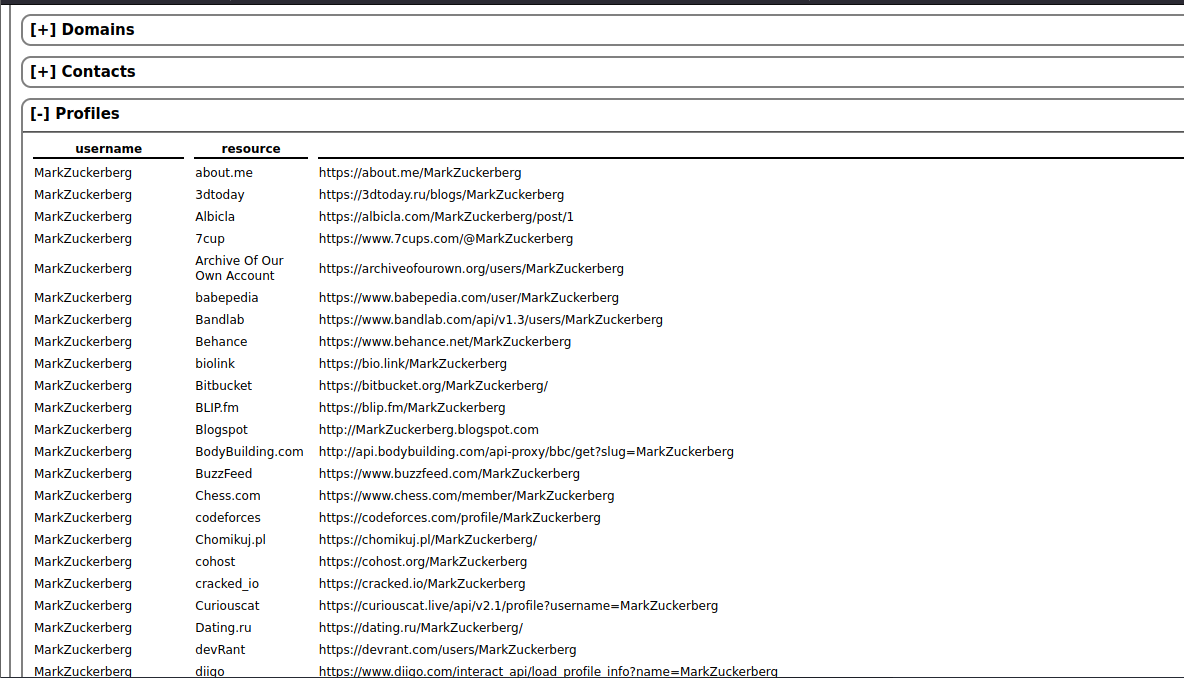
💡Report
Protect Your Digital Presence & Stay Cyber Safe 💙
Thanks🌸