Category: SOC - LetsDefend - FakeGPT Malicious Chrome Extension
 |
| In this writeup, we will investigate the SOC202 - FakeGPT Malicious Chrome Extension |
Alert Phase
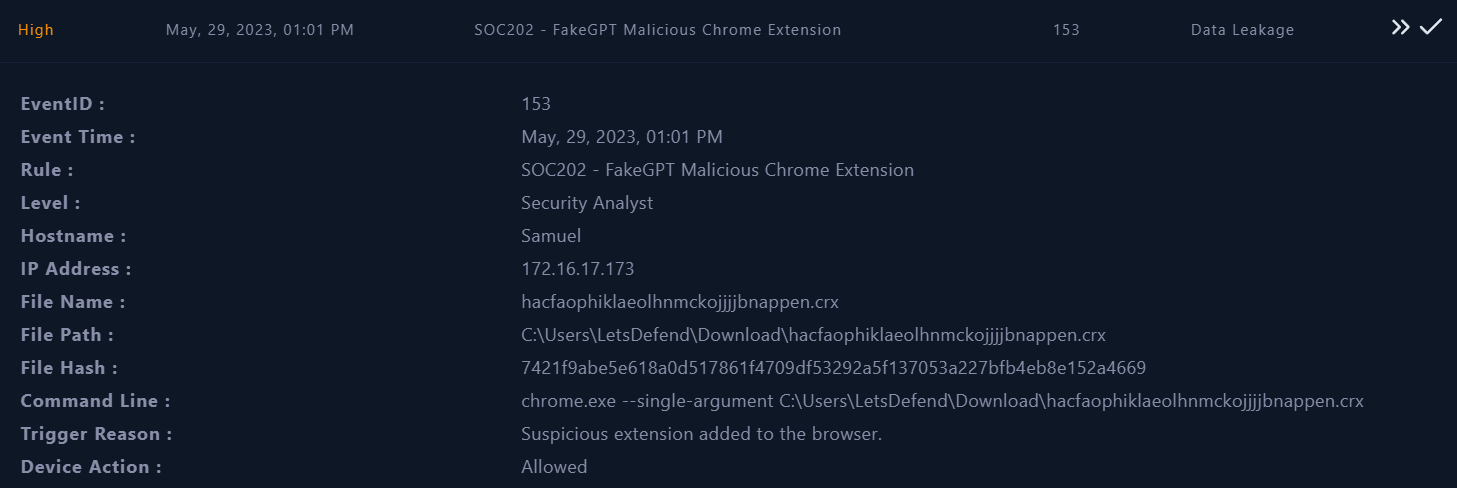 |
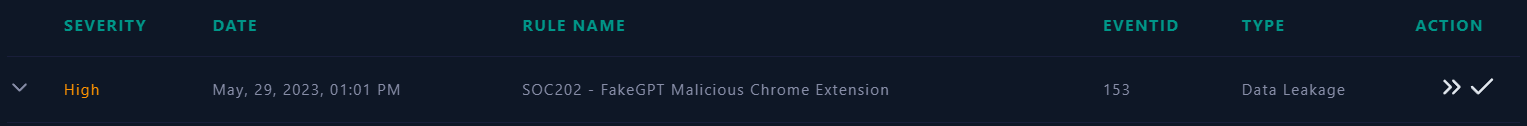
| Screenshot For The Alert |
- We can take a quick look at the “Alert Trigger Reason” in the alert details and understand the root cause of the alert.
- It appears that there is a suspicious file detected on a system named
Samuel with an IP
address of 172.16.17.173.
- The Alert is triggered by the
SOC202 rule for FakeGPT Malicious Chrome Extension.
- Based on this information, it appears that the command line
chrome.exe --single-argument C:\Users\LetsDefend\Download\hacfaophiklaeolhnmckojjjjbnappen.crx is attempting to open or manipulate a Chrome extension file (with the .crx extension hacfaophiklaeolhnmckojjjjbnappen.crx) using the Google Chrome browser.
- The device action is marked as
allowed, indicating that no action was taken by the device to prevent or block the execution of the file.
- Based on the provided Trigger Reason, The browser extension named
hacfaophiklaeolhnmckojjjjbnappen.crx was added, as evidenced by the provided trigger reason. The file hash corresponding to the extension is: 7421f9abe5e618a0d517861f4709df53292a5f137053a227bfb4eb8e152a4669.
In general, there are indications of potential malicious activity on the system, necessitating a thorough investigation to ascertain the full scope of the activity and to devise appropriate measures for remediation.
Detection Phase
- As a security analyst, one of the first steps we take to verify the alert and determine whether it is a false positive or a true positive incident is to analyze the logs collected from the host by our security products.
- The first step we can take to investigate the alert is to examine the system logs of the
Samuel host under Endpoint Security to identify any unusual or suspicious activities that may be related to the reported incident.
- This includes looking for any network connections, browser history or processes initiated around the same time as the suspicious extension installation.
📍 First Let’s Check Processes..
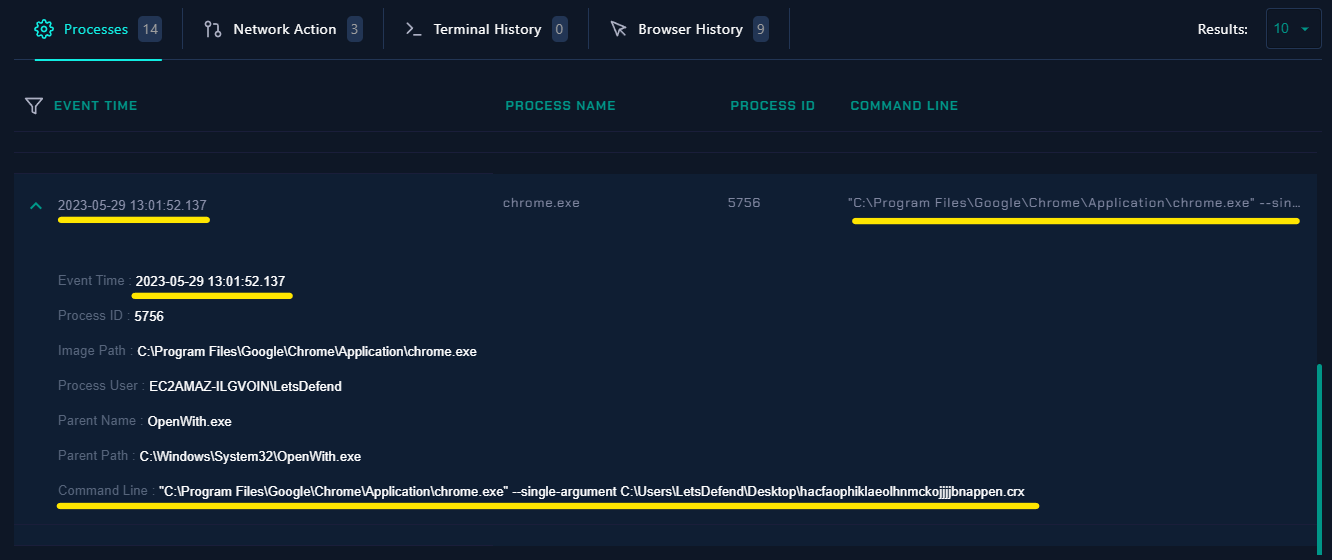 |
| Processes |
📍 Now Let’s Check The Browser History..
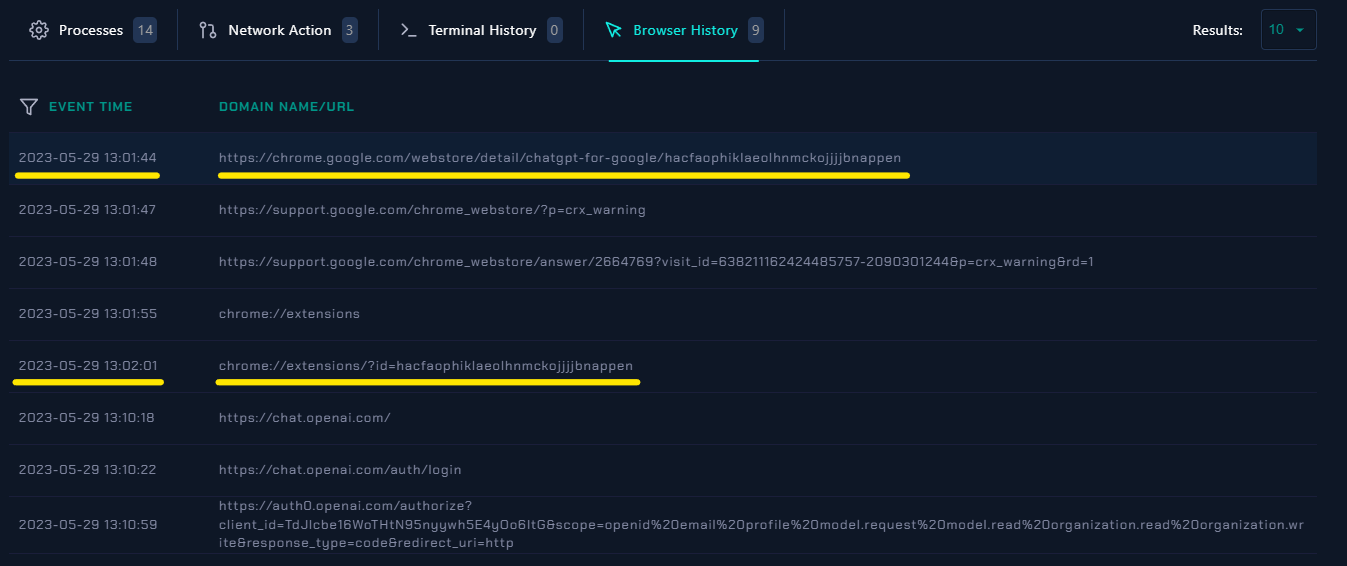 |
| Browser History |
- Based on the browser history, it is evident that the user interacted with the extension and visited various related URLs, including the Chrome Web Store pages and the settings page for the suspicious extension.
- The user visited the Chrome Web Store page for the extension with the URL
https://chrome.google.com/webstore/detail/chatgpt-for-google/hacfaophiklaeolhnmckojjjjbnappen. This indicates that the user accessed the extension’s page on the Web Store.
- The user accessed the Chrome Extensions page, which allows managing installed extensions. This suggests that the user interacted with the extensions settings, possibly to view or modify the installed extensions.
- The user specifically visited the Chrome Extensions page with the extension ID
hacfaophiklaeolhnmckojjjjbnappen. This indicates that the user accessed the settings page for the suspicious extension.
- The user visited the OpenAI Chat platform with URL
https://chat.openai.com/, which is the legitimate website for accessing the ChatGPT-based service.
- The user accessed the login page of the OpenAI Chat platform with URL
https://chat.openai.com/auth/login. Probably for link the suspicious extension to his ChatGPT account.
📍 Finally Let’s Check The Network Connections..
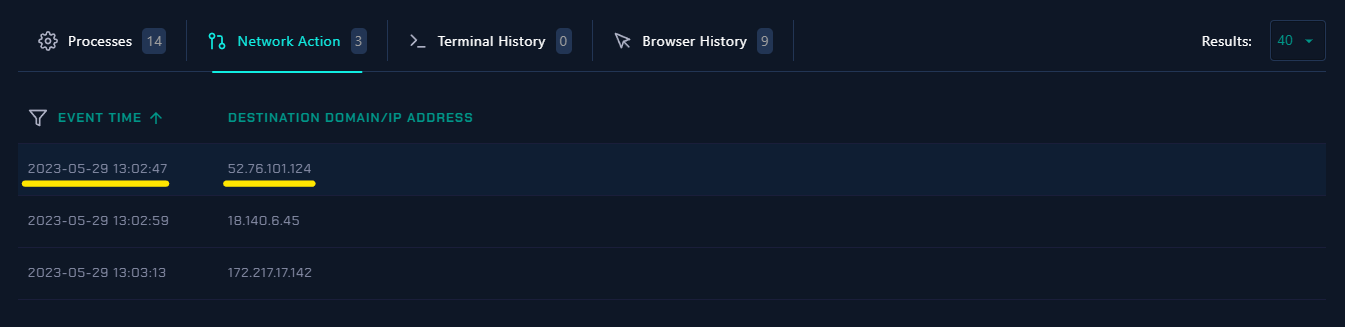 |
| Network Connections |
- Based on the network connections, there are lots of IP addresses that interact with the user.
Analysis Phase
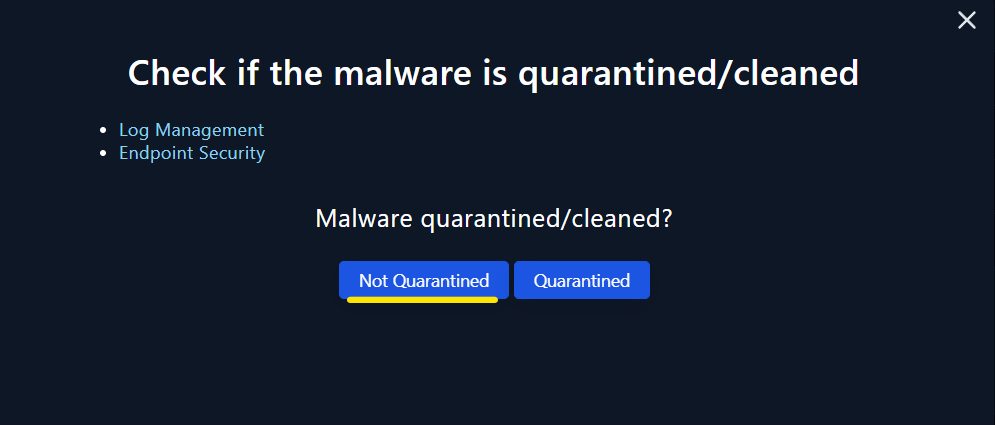 |
| Not Quarantined |
- The fact that the device action was marked as
allowed indicates that no immediate action was taken to quarantine or block the malware. Furthermore, the ongoing network and process activities observed subsequent to the incident also suggest that the malware remains active and has not been successfully quarantined.
VirusTotal
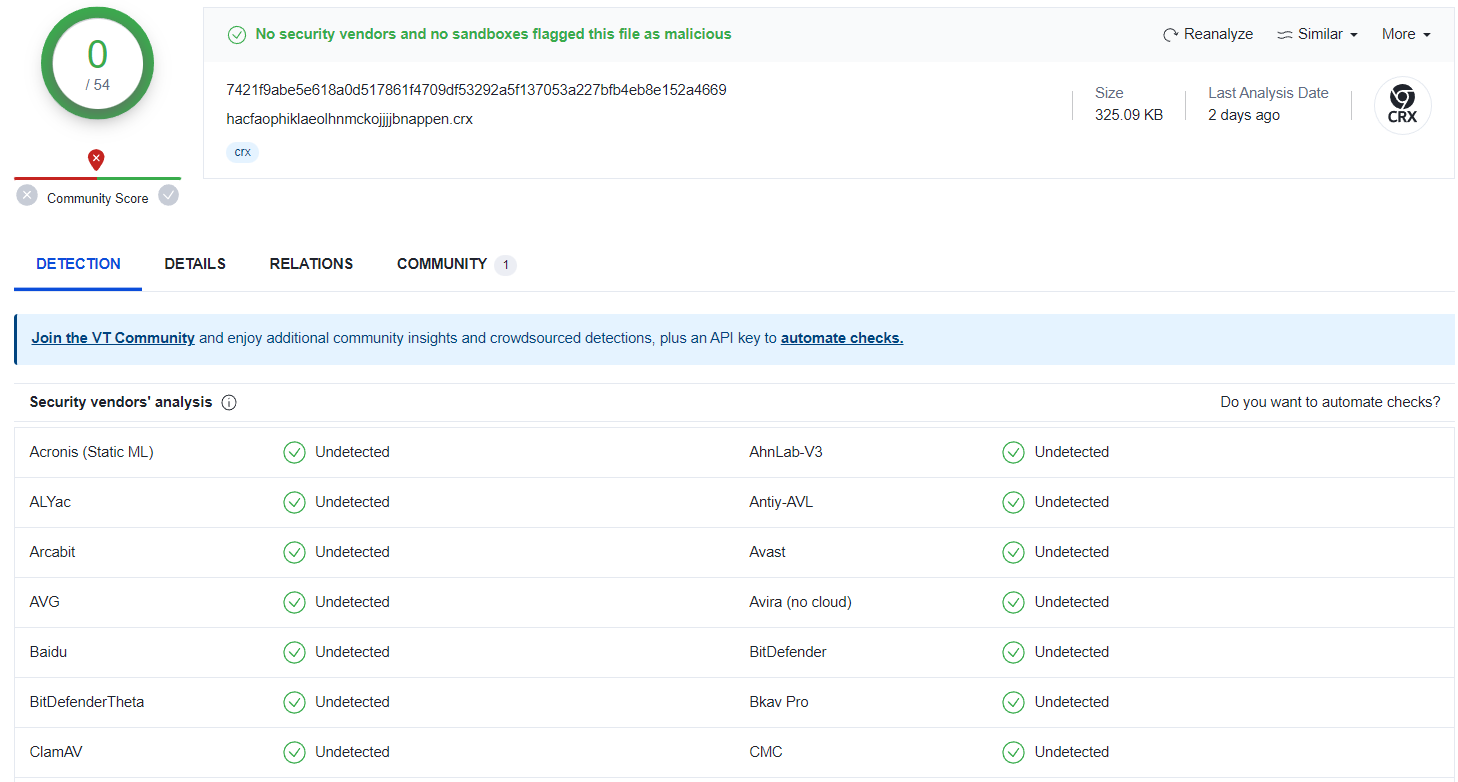
- It is stated in the alert details that the file that exploits the vulnerability is
hacfaophiklaeolhnmckojjjjbnappen.crx. At the same time, we have the hash information of the file. We can quickly search for the hash in Google, Threat Intelligence, and other similar sources and take a look at the results.
- After we submit the file hash in VirusTotal, It does not detect that the file is malicious.
Lets do Deep Analysis in Browser History..
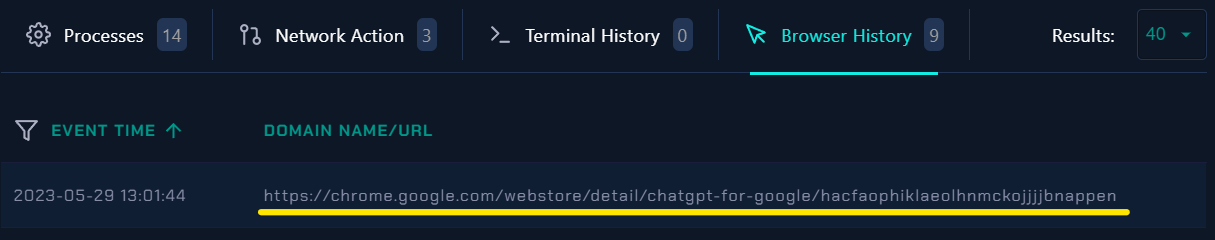 |
| Browser History |
- Based on the provided URL from the browser history the name of the malicious extension is Chatgpt for Google and the ID of the malicious extension is
hacfaophiklaeolhnmckojjjjbnappen.
https://chrome.google.com/webstore/detail/chatgpt-for-google/hacfaophiklaeolhnmckojjjjbnappen
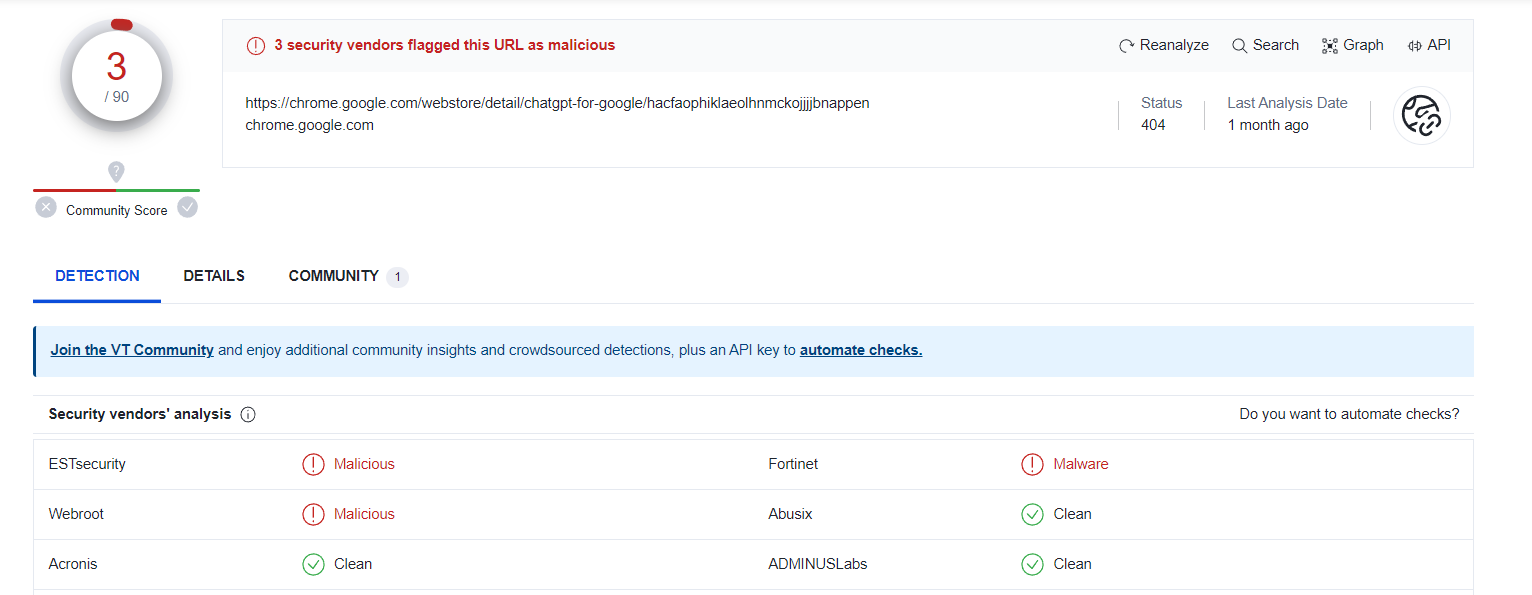
- After we submit the file hash in VirusTotal,, there are total of 3 security vendors flagged this file as malicious.
- During our investigation, attempts to access the URL associated with the malicious extension,
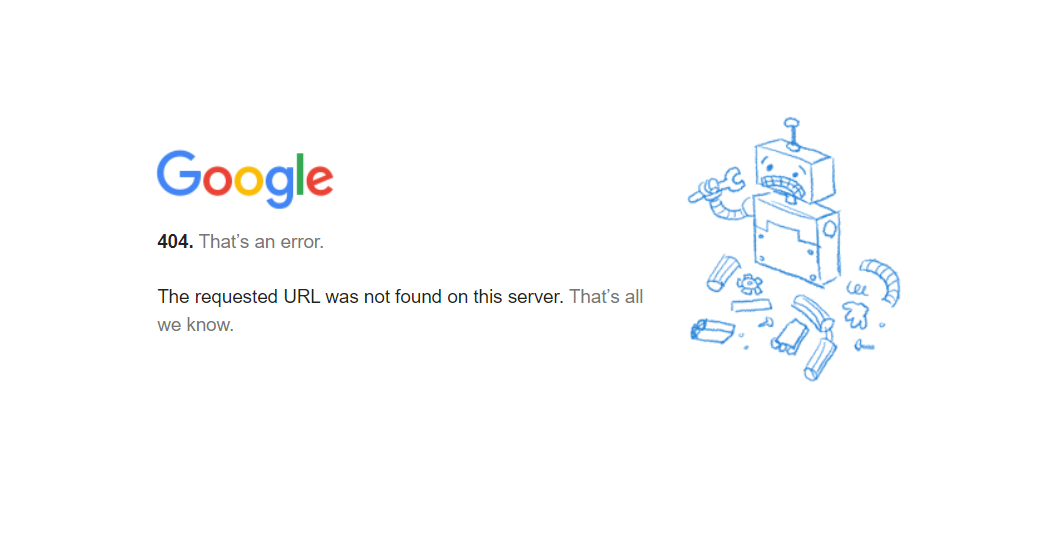
https://chrome.google.com/webstore/detail/chatgpt-for-google/hacfaophiklaeolhnmckojjjjbnappen, resulted in an error message stating “404.
- That’s an error. The requested URL was not found on this server. That’s all we know.” The error message indicates that the specific URL we attempted to access is not currently available on the server. This could suggest that the malicious extension has been removed from the Chrome Web Store or the URL itself is no longer valid.
Compare and analyze Chrome extensions
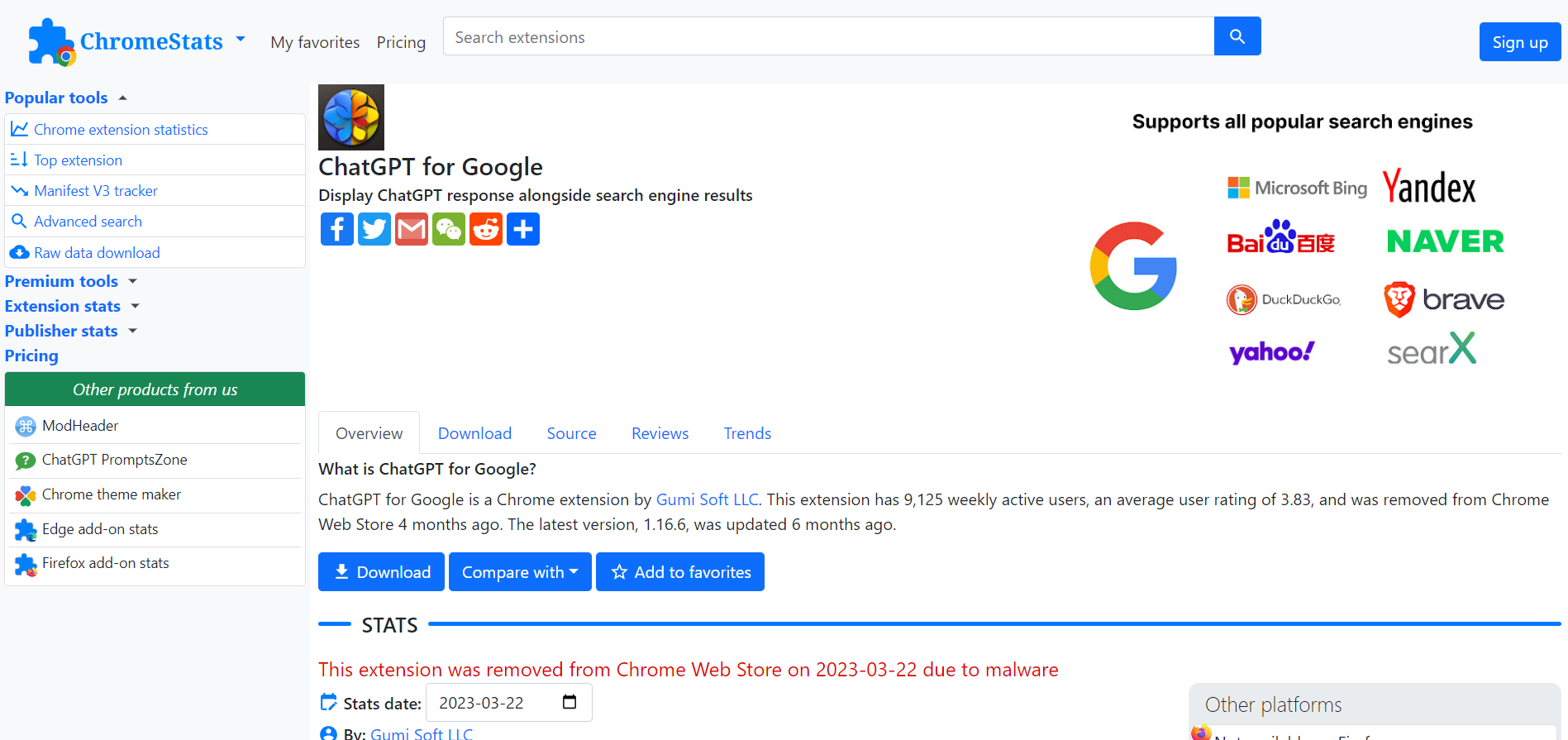 |
| ChromeStats - ChatGPT for Google |
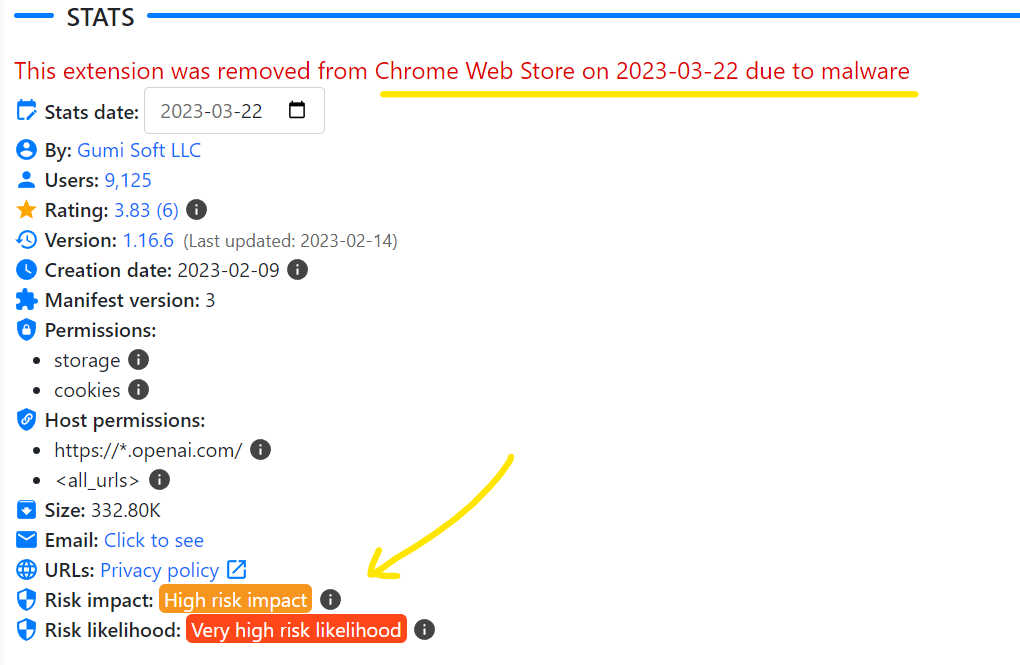
- According to the chrome-stats website, this extension has a high-risk impact and a very high-risk likelihood, indicating significant potential harm and a strong probability of compromising the affected system
 |
| ChromeStats - ChatGPT for Google |
- On 2023-03-22, the malicious extension
hacfaophiklaeolhnmckojjjjbnappen was removed from the Chrome Web Store because it contained malware.
 |
| Analyze Malware |
- The findings from our analysis confirm that the suspicious Chrome extension, identified as
hacfaophiklaeolhnmckojjjjbnappen, is malicious
C2 Access Verification
-
We will analyze the network-based logs collected from the Samuel Host to investigate any indications of Command and Control (C2) access. By examining the network logs, we aim to identify any suspicious connections or communication patterns that may suggest unauthorized interactions with the C2 infrastructure.
-
On Log Management tab we filter the source address to the Ip address of Samuel Host 172.16.17.173 to see the logs related of the given ip address.
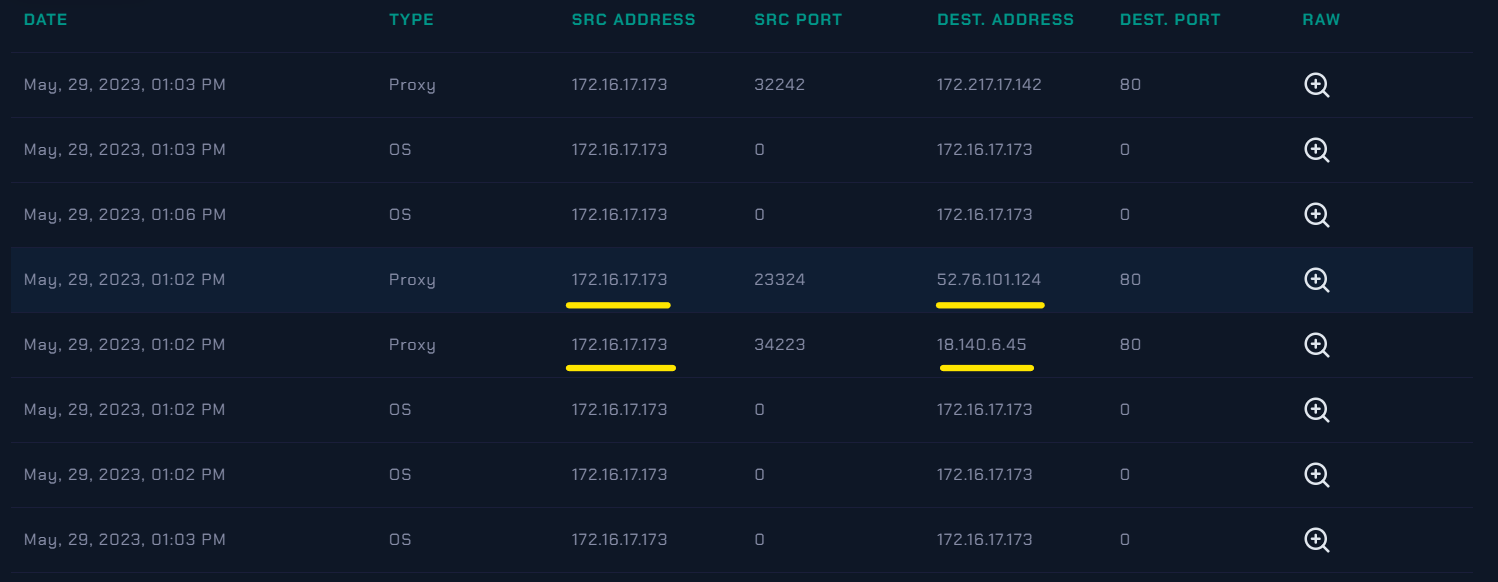 |
| Log Management |
The raw log of the event are as follows:
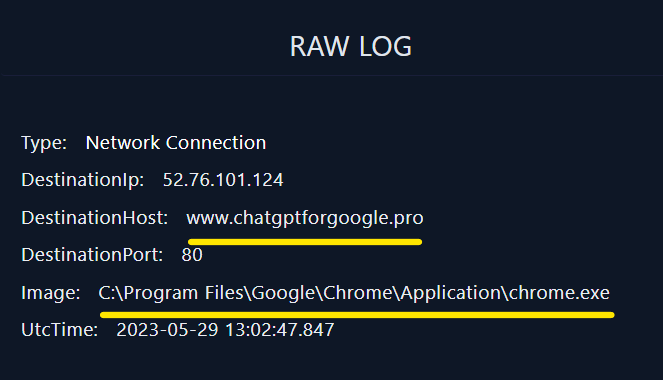 |
| RAW LOG |
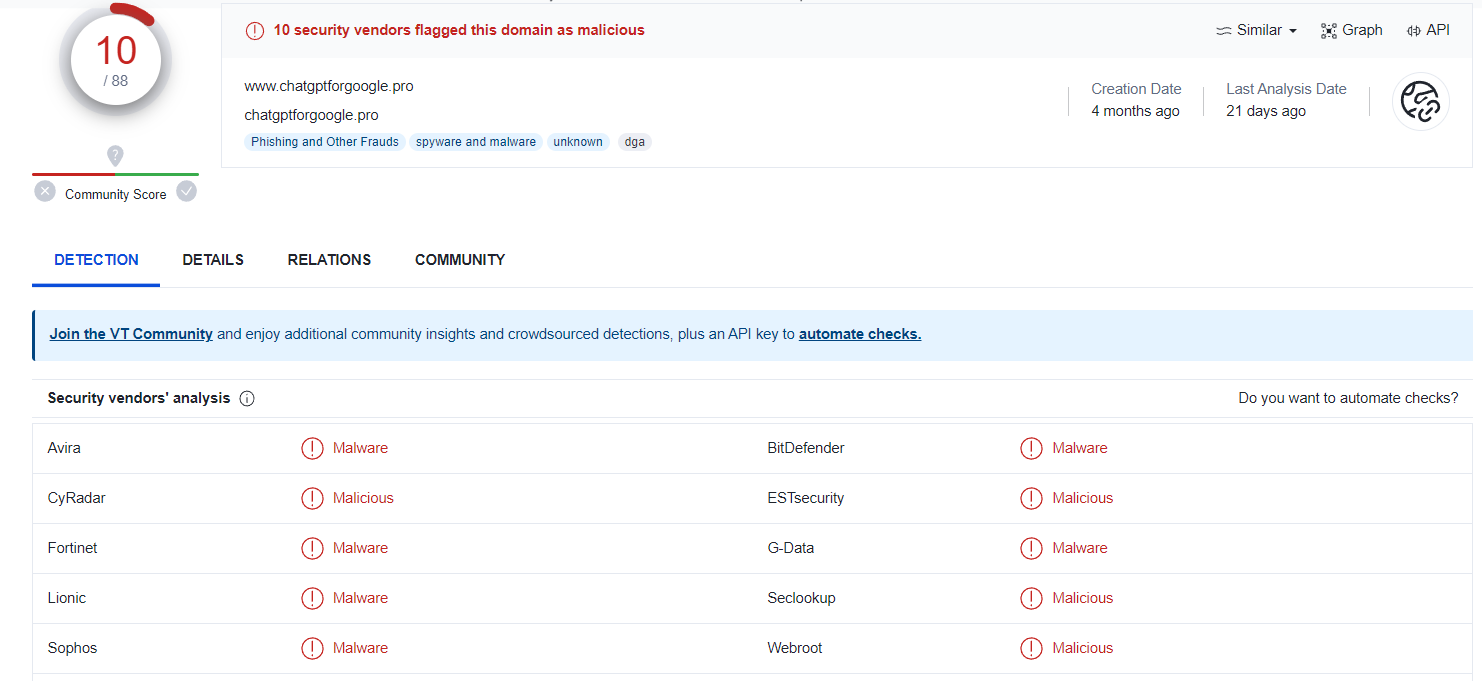
- Further investigation of the domain “www.chatgptforgoogle.pro” on threat intelligence platforms, such as VirusTotal, confirms its malicious nature.
- The findings from these platforms indicate that the URL is associated with known malicious activity and has been reported as a threat.
-
After we submit the file hash in VirusTotal,, there are total of 10 security vendors flagged this file as malicious.
-
The analysis of the C2 communication attempts associated with the suspicious extension indicates a high likelihood of malicious intent. The identified connections to chatgptforgoogle.pro, chatgptgoogle.org, and version.chatgpt4google.workers.dev highlight the need for immediate action to mitigate the threat and prevent further compromise.
 |
| Accessed C2 |
Containment Phase
- We found solid evidence that the
Samuel device was compromised. Now, we need to isolate the device from the network in order to prevent the attacker from reaching different devices in the internal network and to break its existing connection.
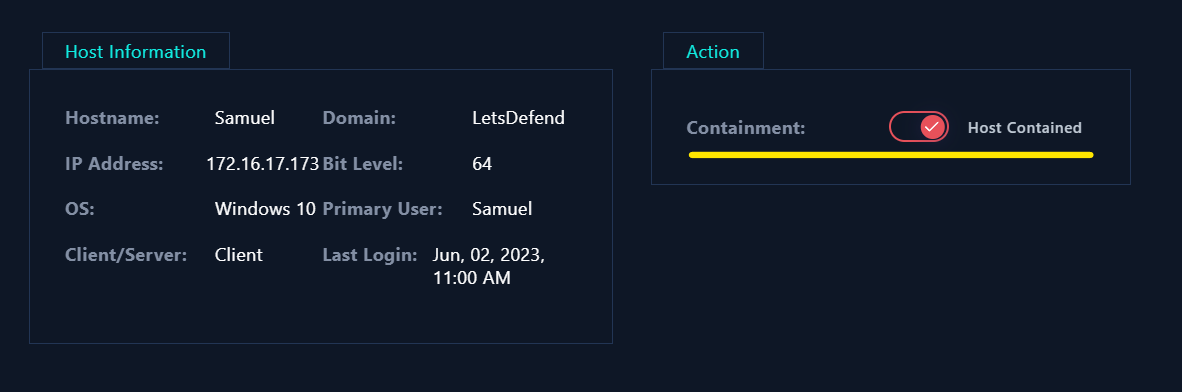 |
| Containment |
Lesson Learned
- Vigilant user awareness and caution are of utmost importance during browser extension installations.
- Maintaining up-to-date software is essential to minimize vulnerabilities and exposure to known exploits
- Swiftly investigate and respond to any suspicious extension installations.
- Continuously learn from incidents to adapt and fortify security measures against emerging threats.
- Remove the malicious extension from affected systems.
- Isolate the compromised machine from the network to prevent the attacker from accessing other resources and systems within the organization.
- Review and update security configurations to enhance protection against similar threats in the future.
- Reset affected user accounts, including passwords, and enable two-factor authentication where available
Artifacts
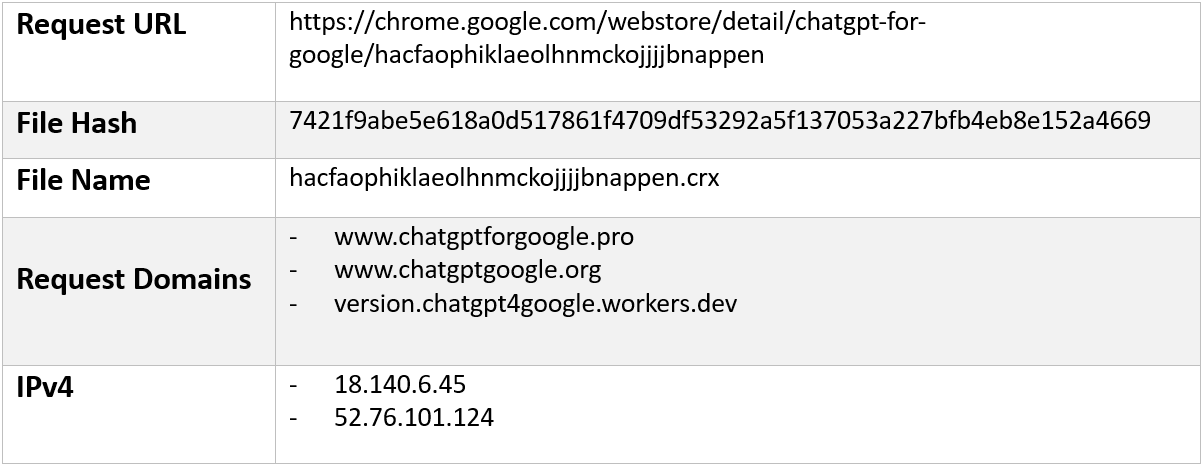 |
| Artifacts |
Closed Alert
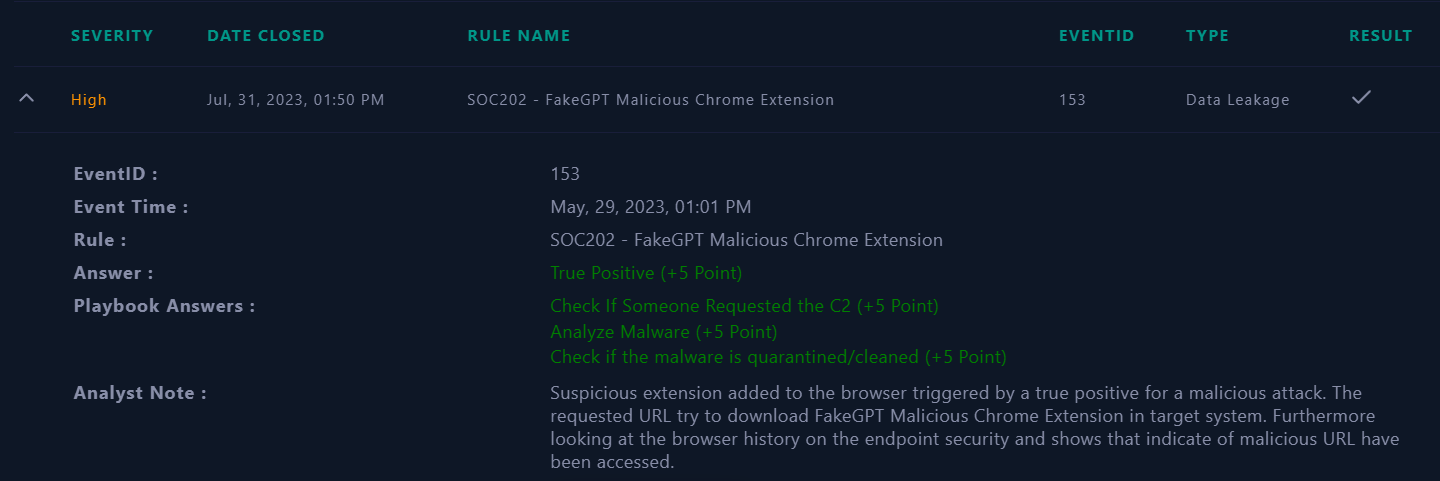 |
| Closed Alert |
We see our results. Woohoo! All correct! No one is perfect all the time however, and if you missed anything you can always re-investigate the case.

Protect Your Digital Presence & Stay Cyber Safe 💙
Thanks🌸