Category: SOC - LetsDefend - Data Breach
Alert Phase
 |
|---|
| In this writeup, we will investigate the Mysterious Data Breach |
Answer This Questions
- Malicious file Name? (Easy)
- Which programming language is the backdoor written in? (Easy)
- Backdoor name? (Medium)
- Who is the author of backdoor? (Medium)
- What is command&control IP address? (Medium)
- Which user’s password leaked except Administrator user? (Medium)
- Which tool triggered the reverse shell? (Hard)
- What is the MD5 of backdoor? (Hard)
Detection Phase
- First we looking for anyone in company called
Andersonby checking the Endpoint Security.
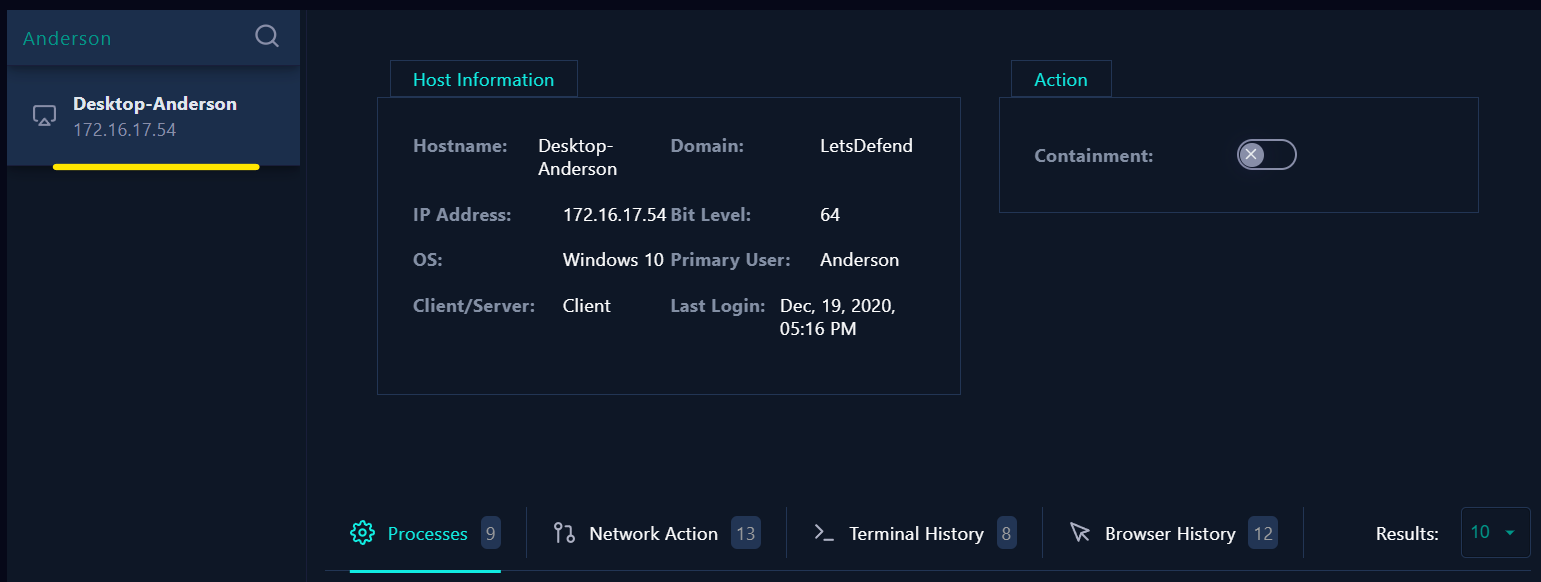
- After we check the
Endpoint Securitywe found the device calledDesktop-Anderson. -
Now we check and analyis all Processes, Network Action, Terminal History and Browser History in
Desktop-Anderson. - Based on above information:
- Hostname: Desktop-Anderson
- IP Address: 172.16.17.54
- OS: Windows 10
- Primary User: Anderson
First Let’s Check Processes
 |
|---|
| Processes |
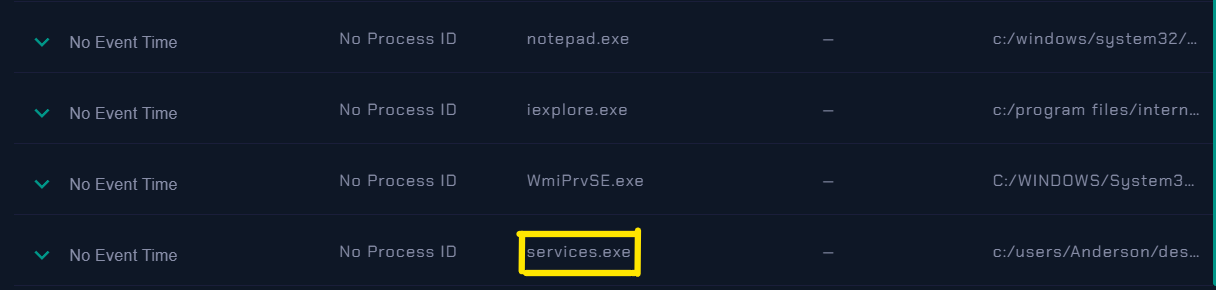
The path you’ve provided, C:/Users/Anderson/Desktop/services.exe is a file system path on a Windows operating system. This path points to a specific executable file located on the desktop of the user account named Anderson.
- services.exe: This is the specific executable file you’re referencing.
services.exeis a critical system process in Windows that manages various system services. It’s an essential component of the Windows operating system.
However, it’s important to note that
services.exeis also a commonly exploited filename used by malware. Legitimate “services.exe” is located in theC:/Windows/System32directory. If you encounterservices.exein an unusual location like a user’s desktop, it could potentially indicate malware or suspicious activity.
Now lets go deep inside this process and see more information about this:
 |
|---|
| service.exe |
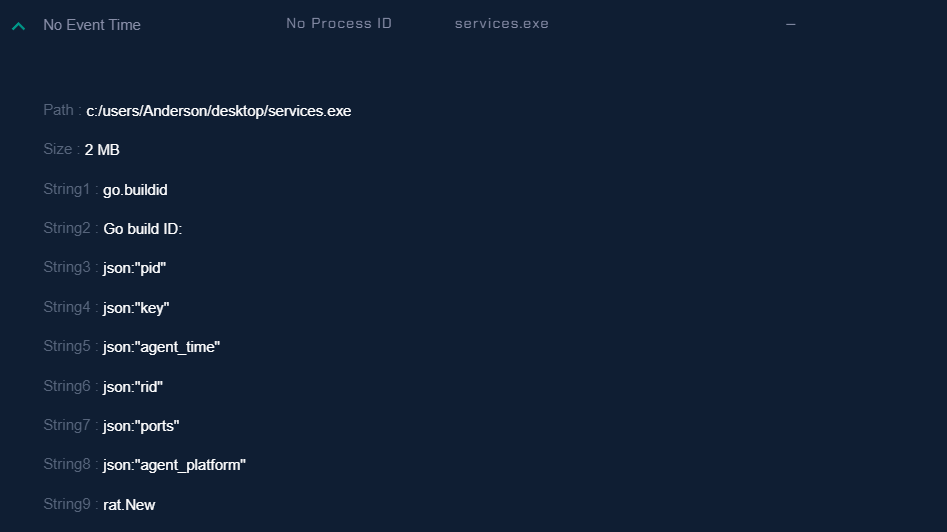
- Based on the provided strings, such as
Go build IDand theGo-specificsyntax used in the string annotations, it appears that the fileservices.exeis likely written in the Go programming language.
Then Let’s Check Network Action
 |
|---|
| Network Connections |
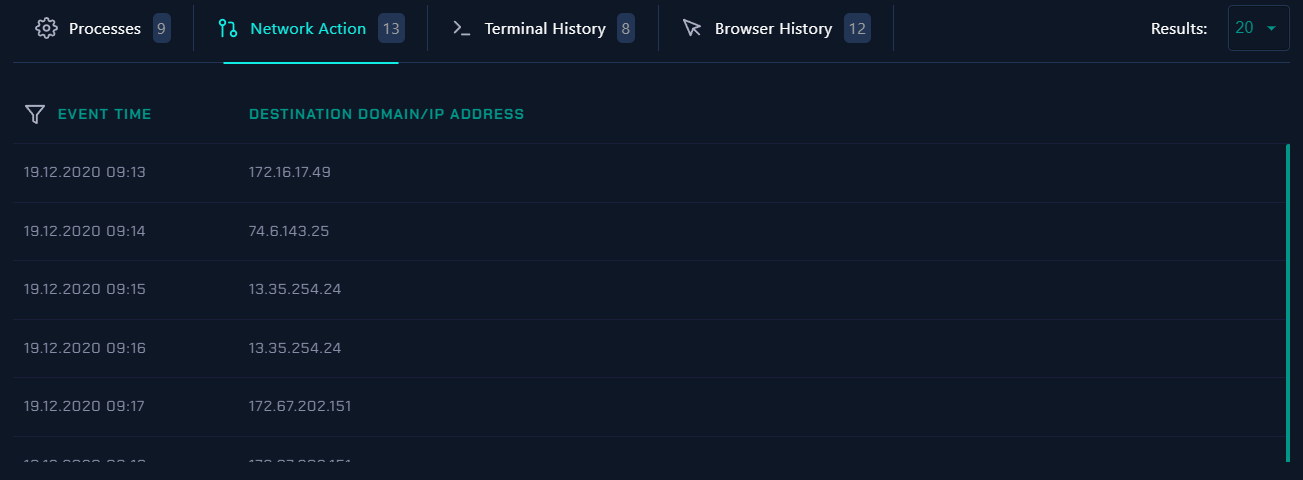
- The IP Address that anderson interact with:
- 🚩 172.16.17.49 (Malicious)
- 74.6.143.25
- 13.35.254.24
- 172.67.202.151
- 🚩 161.35.41.241 (Malicious)
- 172.67.202.151
Later we check the Log Management to check this IPs Logs.
Then Let’s Check Terminal History
 |
|---|
| Terminal History |
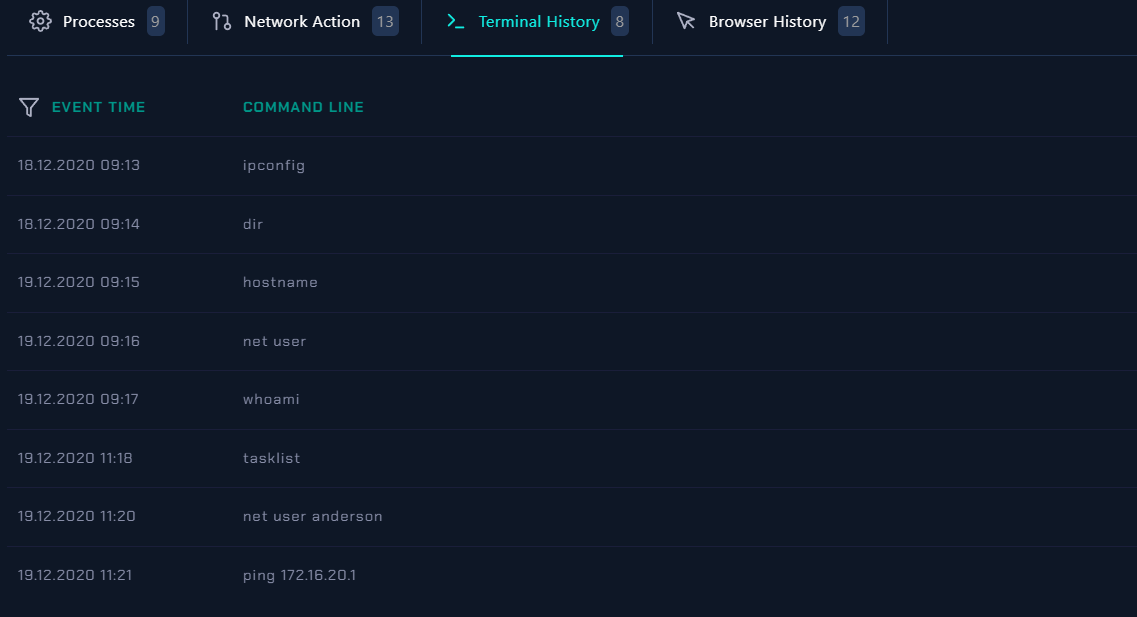
It looks like you’ve provided a list of command-line commands along with timestamps. These commands are often used in the Windows Command Prompt to perform various system-related tasks.
- I’ll explain each command for you:
- ipconfig:
- This command is used to display the IP configuration settings of the computer, including information about network interfaces, IP addresses, subnet masks, and more.
- dir:
- The
dircommand is used to list the files and subdirectories in the current directory.
- The
- hostname:
- This command displays the name of the computer within a network.
- net user:
- The
net usercommand is used to manage user accounts on the system. Without additional parameters, it typically displays a list of user accounts on the computer.
- The
- whoami:
- This command displays the username of the currently logged-in user.
- tasklist:
- The
tasklistcommand displays a list of running processes and their associated information.
- The
- net user anderson:
- This command queries the user account information for the user named
anderson.
- This command queries the user account information for the user named
- ping 172.16.20.1:
- The
pingcommand is used to test network connectivity to a specific IP address (in this case, 172.16.20.1). It sends a series of network packets to the specified IP address and measures the response time.
- The
- ipconfig:
Checking Log Management
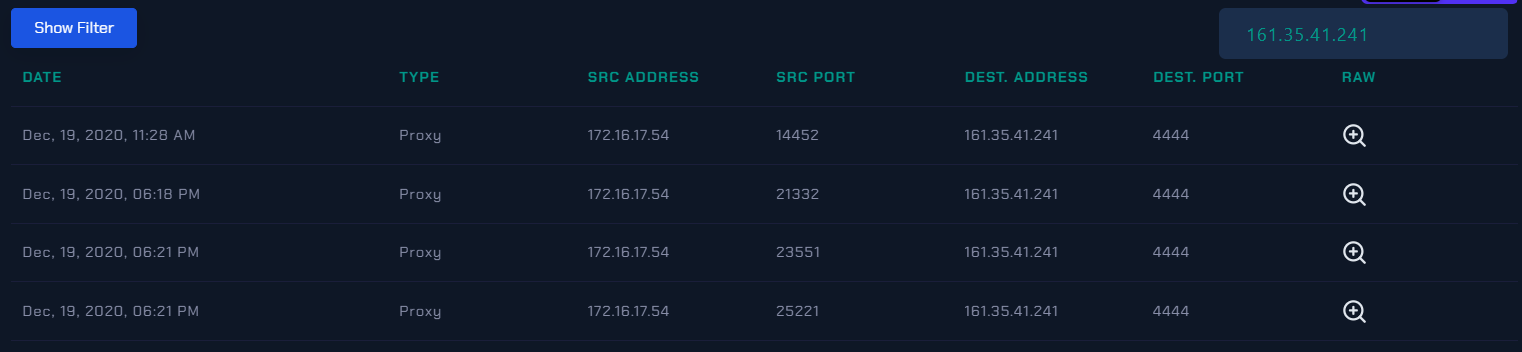
🚩 Now we check the IP address 161.35.41.241:
 |
|---|
| Log Management |
From above logs, lets try to check logs:
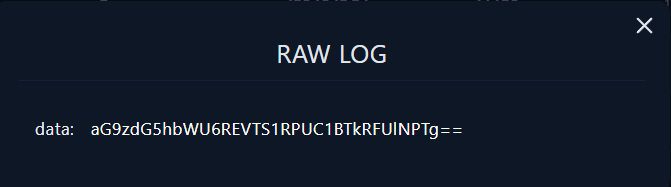
This data encoded using Base64, lets try to decode this data by using cyberchef
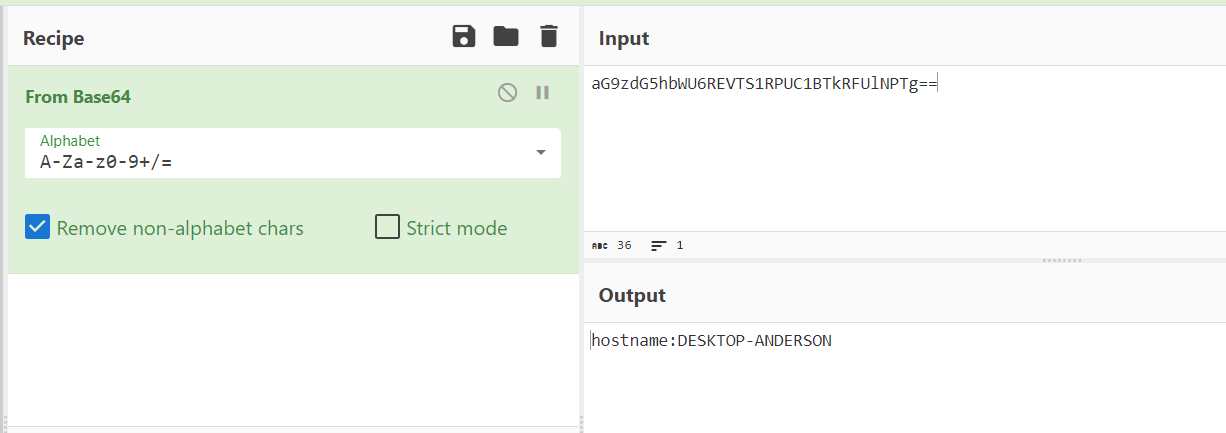 |
|---|
| cyberchef |
- Do above proccess for all above log and show secret data 😉
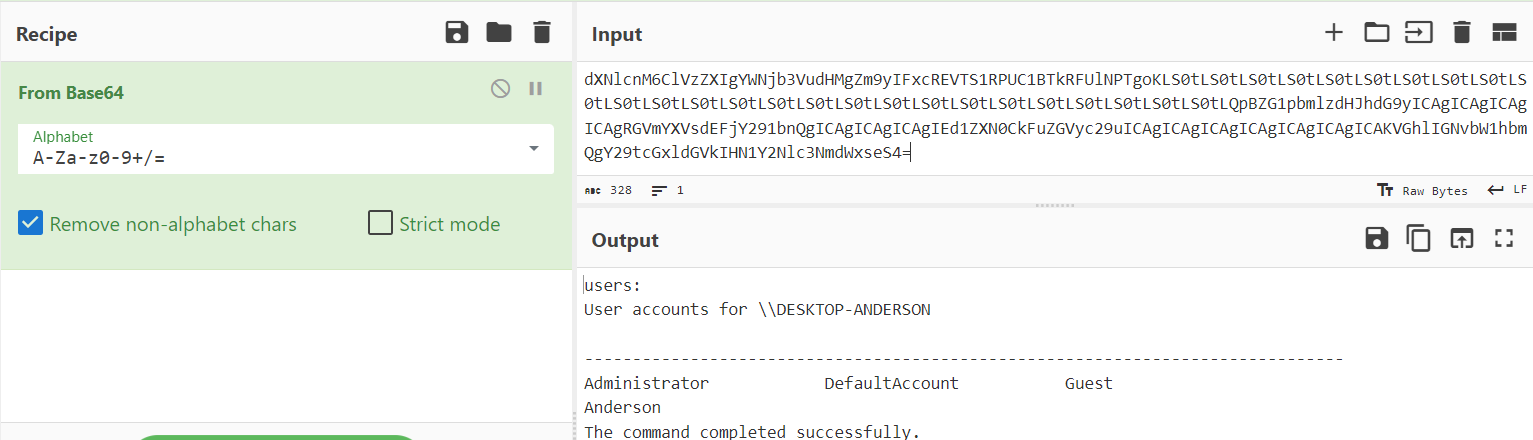 |
|---|
| cyberchef |
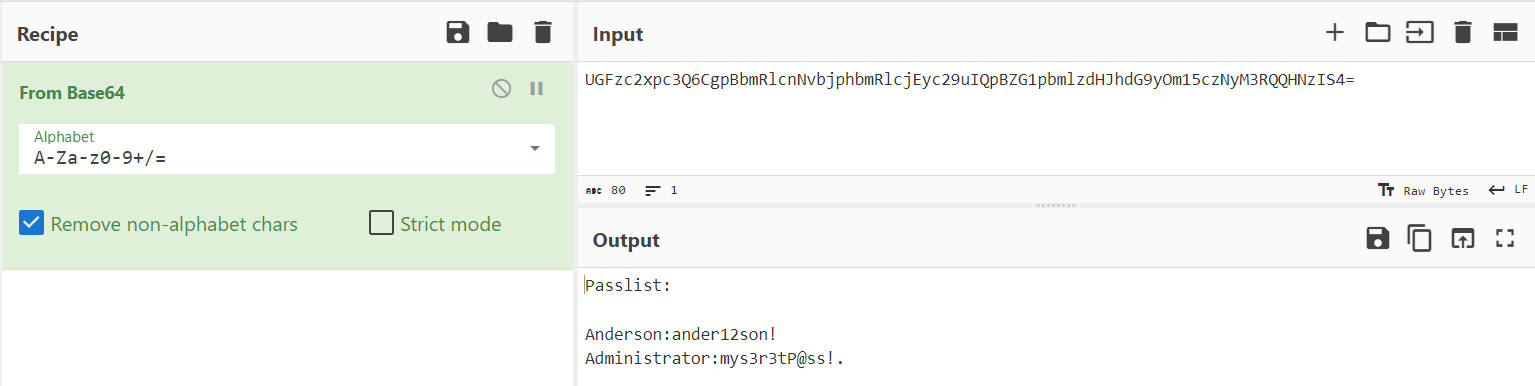 |
|---|
| cyberchef |
🚩 Checking the first log:
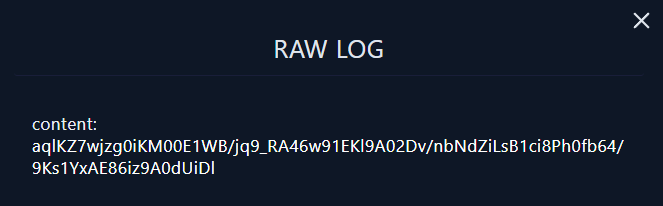
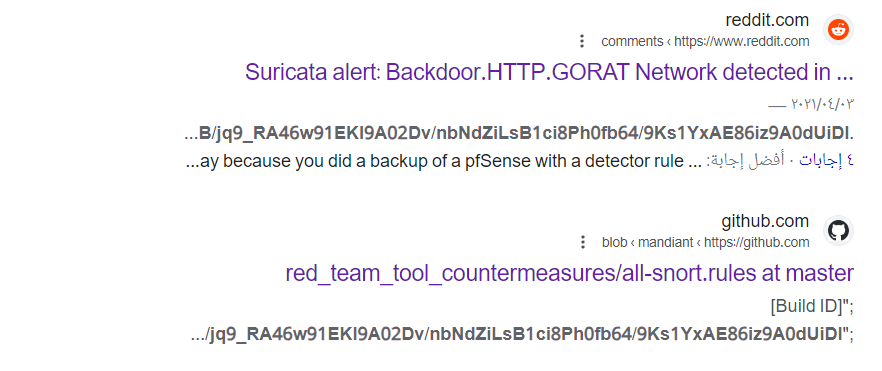
- Now we can take this content
aqlKZ7wjzg0iKM00E1WB/jq9_RA46w91EKl9A02Dv/nbNdZiLsB1ci8Ph0fb64/9Ks1YxAE86iz9A0dUiDland google it, and lets show the results
 |
|---|
- Check this two links and use it for answering the hard questions.
Usefull links:
Artifacts
- IP Addresses
- 161.35.41.241
- 172.16.17.49
- Hashes
- f59095f0ab15f26a1ead7eed8cdb4902
Flags
1. Malicious file Name? (Easy)
services.exe2. Which programming language is the backdoor written in? (Easy)
Go programming language3. Backdoor name? (Medium)
HTTP.GORAT4. Who is the author of backdoor? (Medium)
FireEye5. What is command&control IP address? (Medium)
161.35.41.2416. Which user’s password leaked except Administrator user? (Medium)
- Anderson:ander12son!- Administrator:mys3r3tP@ss!
7. Which tool triggered the reverse shell? (Hard)
impacket8. What is the MD5 of backdoor? (Hard)
f59095f0ab15f26a1ead7eed8cdb4902Protect Your Digital Presence & Stay Cyber Safe 💙
Thanks🌸