Category: SOC - LetsDefend - Phishing Mail
 |
|---|
| SOC146 - Phishing Mail Detected - Excel 4.0 Macros |
In this writeup, we will investigate the Excel 4.0 Macros vulnerability — Phishing Mail Detected. For those who are not aware of what Excel 4.0 Macros is, this link provides a comprehensive overview of the vulnerability.
 |
|---|
| Screenshot For The Alert |
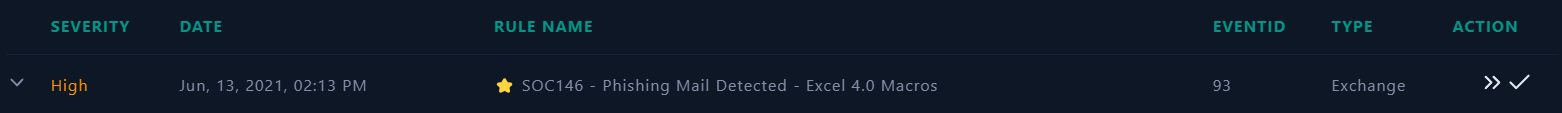
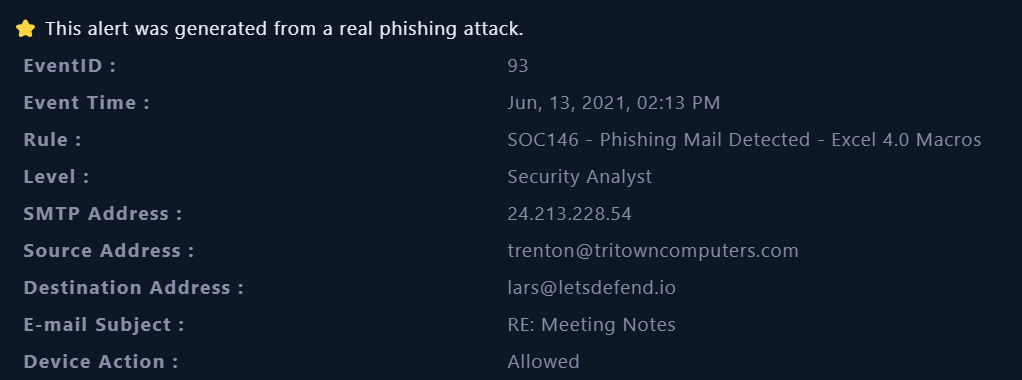
Metadata information of the event which triggered the SIEM alert:
- For this alert, we see that a suspicious behaviour that hit the
SOC146 - Phishing Mail Detected - Excel 4.0 Macrosrule, we can also see the Source Address, SMTP address, Destination Address and E-mail Subject.
Let’s get ready to investigate the alert..!
- The first step is to copy the sender address and look for it in our
Email Security. we find the copy of the email that generated the alert.
 |
|---|
| Email Security |
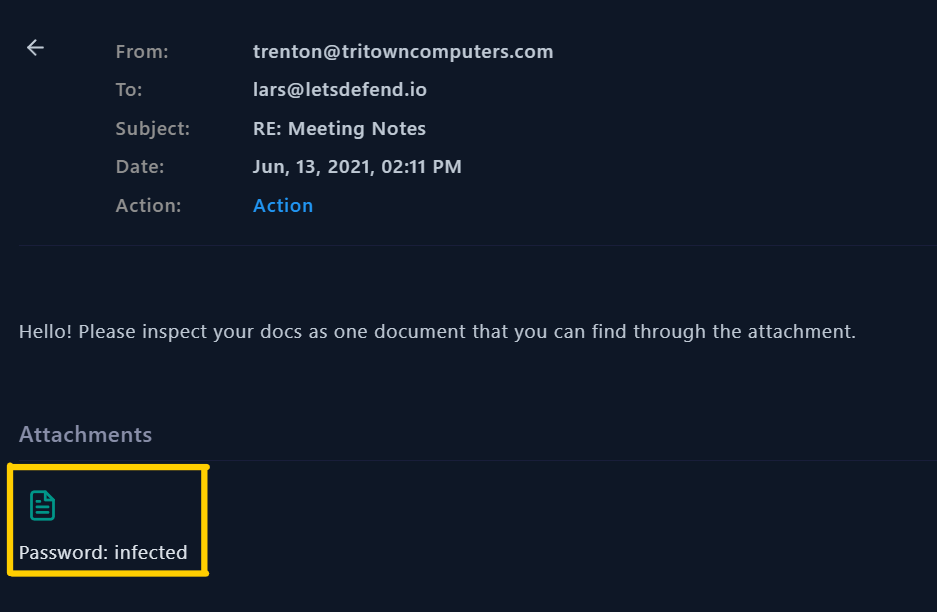
Lets open this mail:
 |
|---|
| MailBox of trenton |
⛳Important information found in the email
- Subject: RE: Meeting Notes
- From: trenton@tritowncomputers.com
- To: lars@letsdefend.com
- Attachment: 11f44531fb088d31307d87b01e8eabff.zip
Next, we will download the attachment file in isolated environment and unzip the file, I’m using ParrotOS
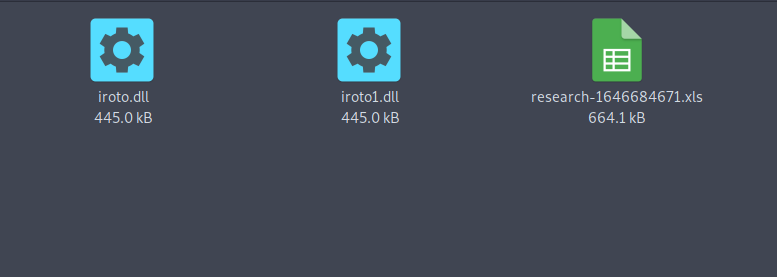
After unzipping the attachment, we found three files:
- iroto.dll
- iroto1.dll
- research-1646684671.xls
 |
|---|
| 11f44531fb088d31307d87b01e8eabff.zip files |
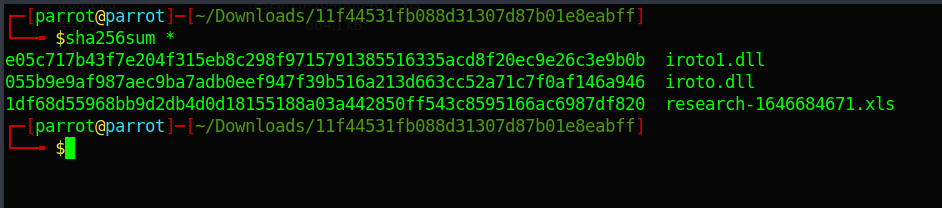
By using sha256sum we will calculate the hash of each file in the attachment 11f44531fb088d31307d87b01e8eabff.zip
 |
|---|
| sha256sum |
Now we can put the hashs of the files in Virus Total to get a preliminary overview of whether the file is malicious or not and to see if there are any hits returned.
- e05c717b43f7e204f315eb8c298f9715791385516335acd8f20ec9e26c3e9b0b iroto1.dll
- 055b9e9af987aec9ba7adb0eef947f39b516a213d663cc52a71c7f0af146a946 iroto.dll
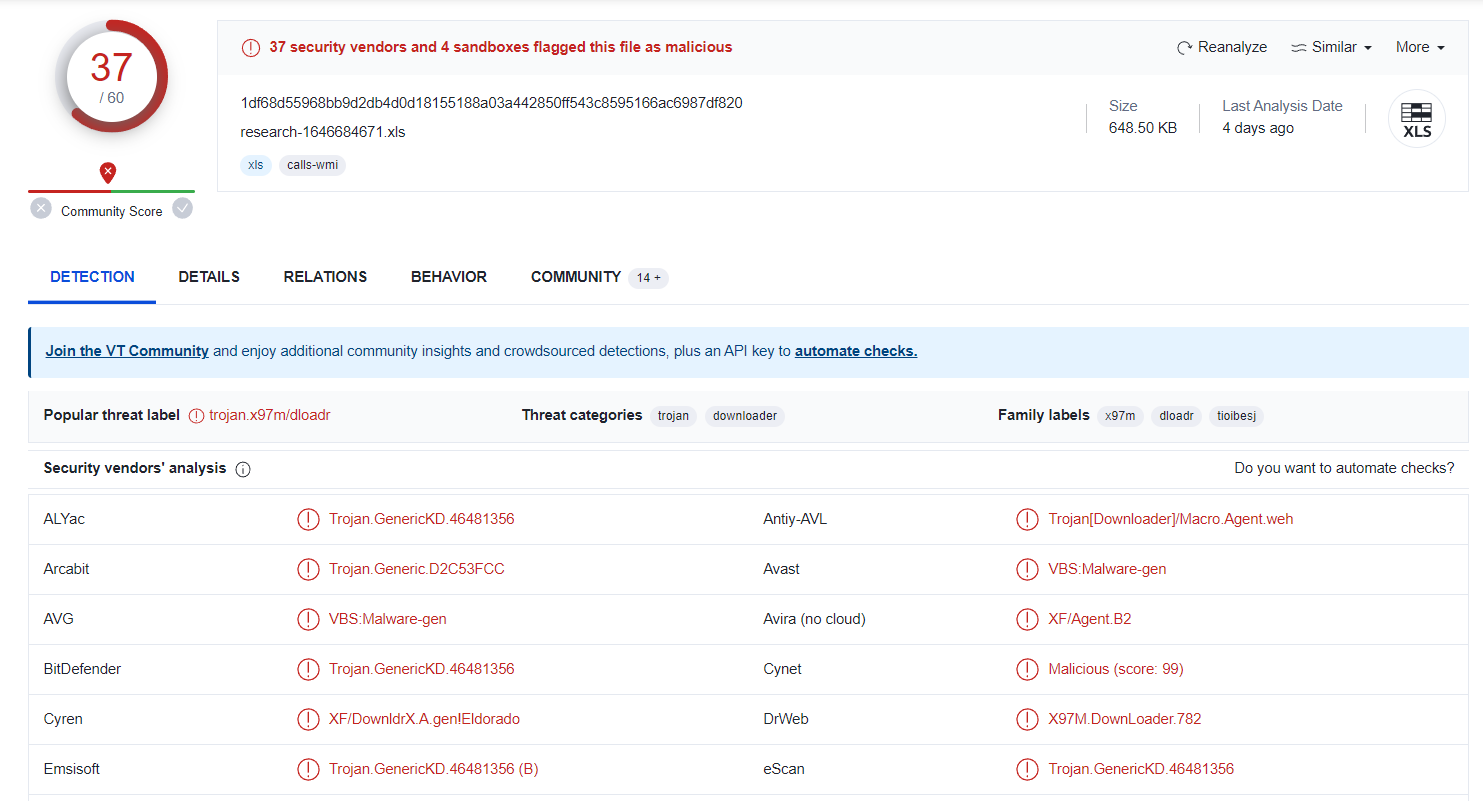
- 1df68d55968bb9d2db4d0d18155188a03a442850ff543c8595166ac6987df820 research-1646684671.xls
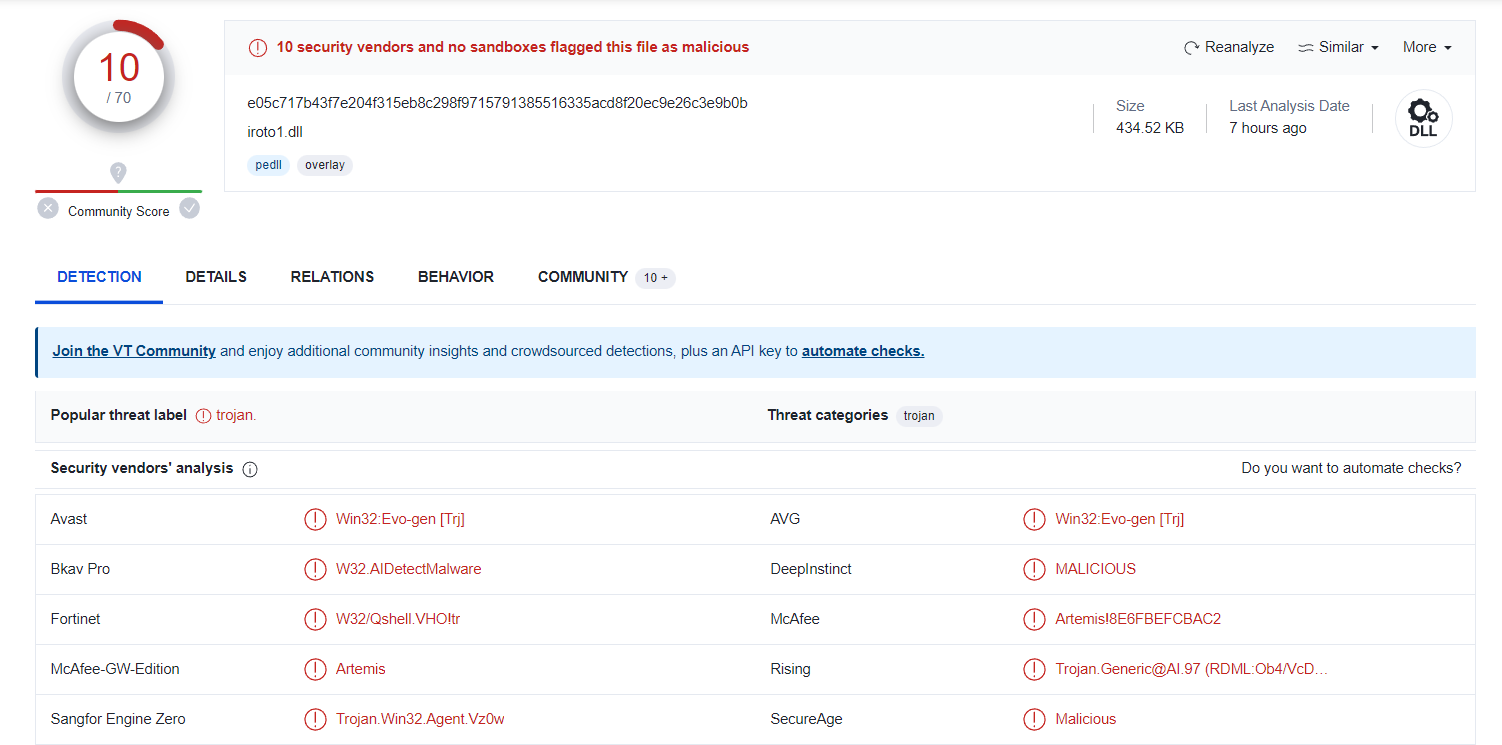
iroto1.dll
 |
|---|
| iroto1.dll seems to be very malicious |
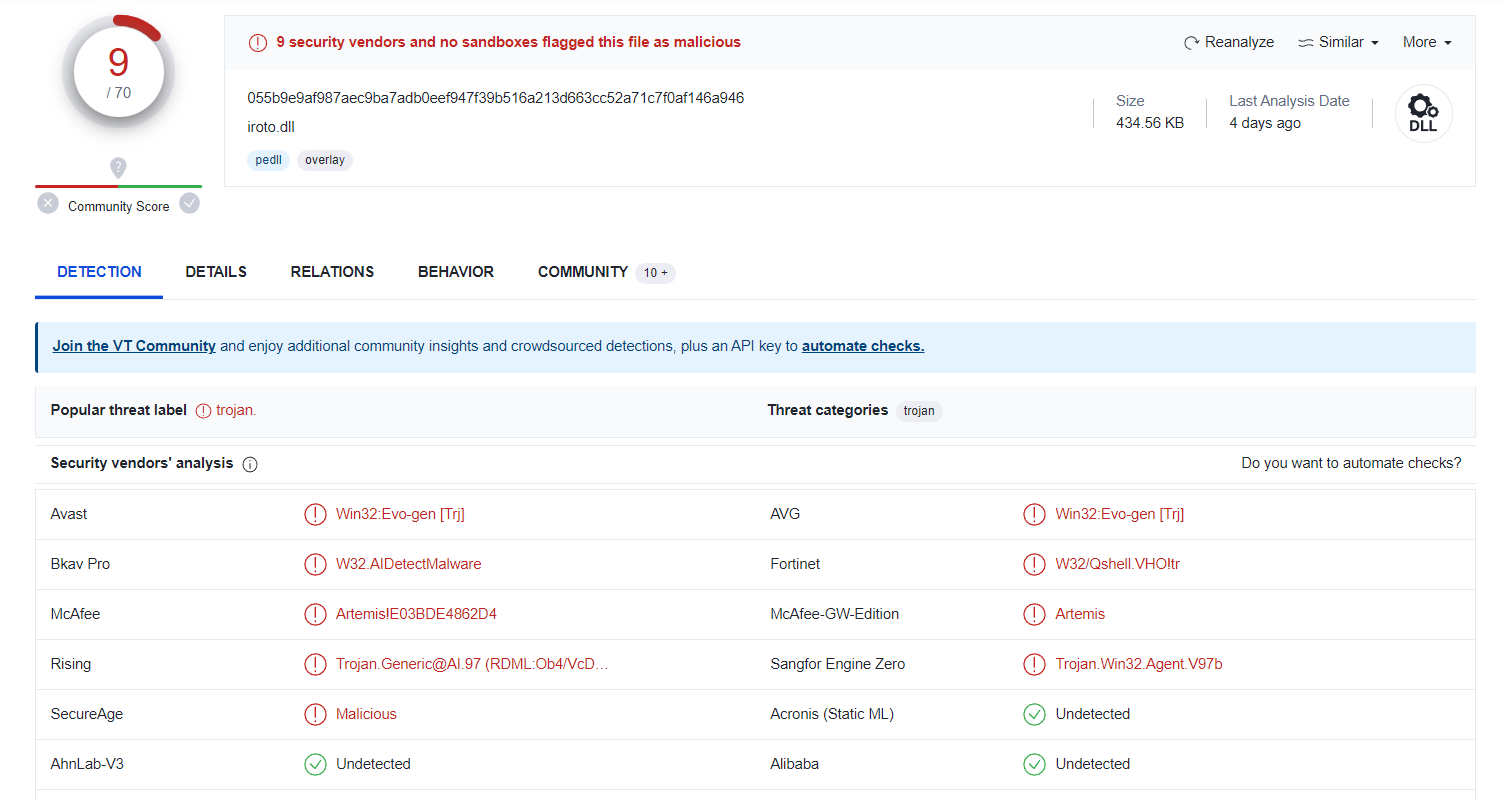
iroto.dll
 |
|---|
| iroto.dll seems to be very malicious |
research-1646684671.xls
 |
|---|
| research-1646684671.xls seems to be very malicious |
According to VT, the three files are flagged malicious:
- The result reports 37 antivirus engines claiming the excel file has malicious.
- And 19 different antivirus engines claiming the DLL is malicious.
ANY.RUN
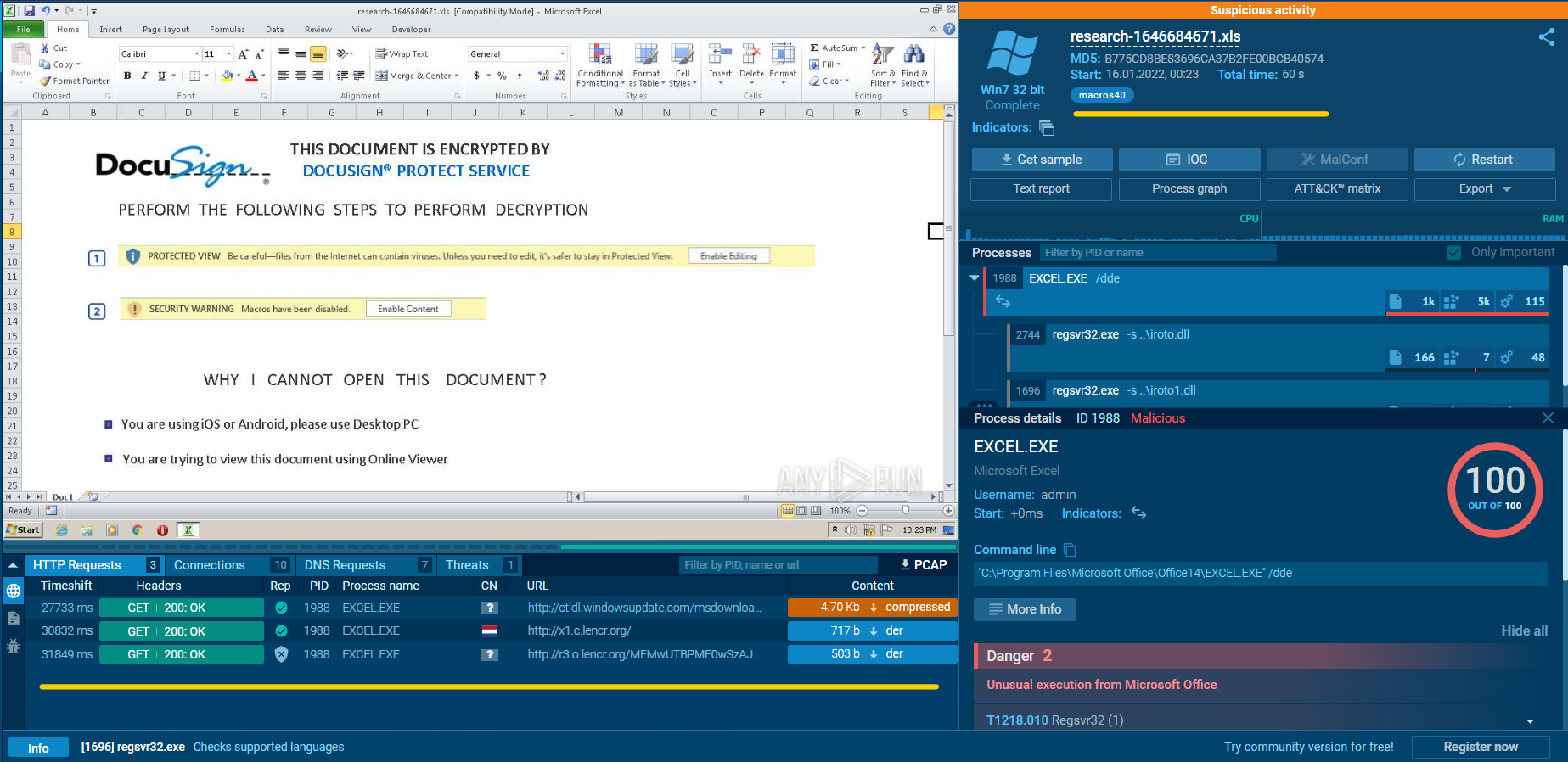
Next, we will simulate this artefact’s behaviour on compromised system by submitting it to ANY.RUN
💡Look at ANY.RUN report from here
 |
|---|
| research-1646684671.xls ANY.RUN Analysis |
Behavior Graph
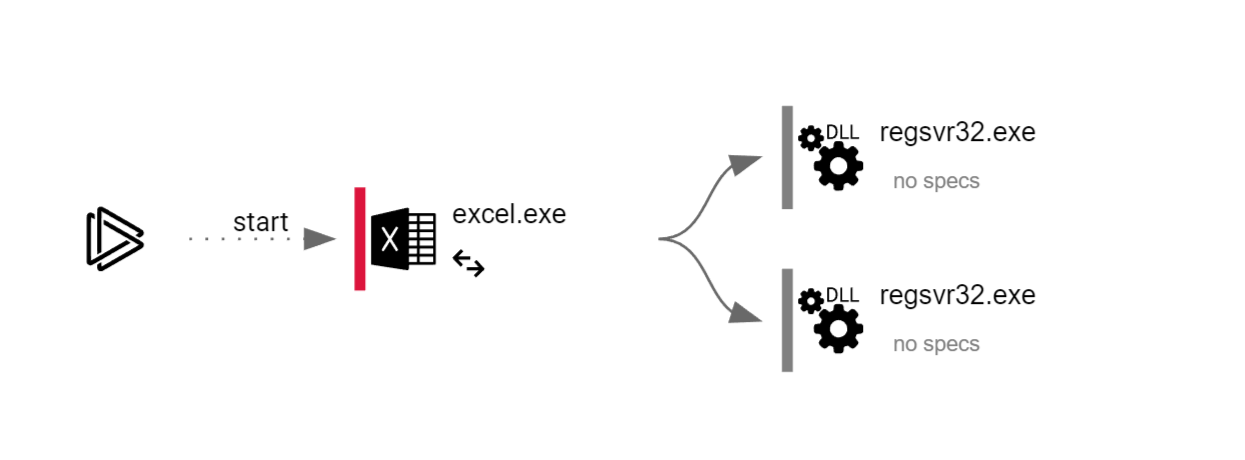 |
|---|
| Behavior Graph |
The malicious use of Regsvr32.exe can bypass security tools that might not actively monitor the execution of the regsvr32.exe process or the modules loaded by it. This can occur due to allowlists or false positives from Windows, as regsvr32.exe is commonly used for legitimate operations.
Regsvr32.exe
- Regsvr32.exe is a command-line utility in the Windows operating system used for registering and unregistering Dynamic Link Libraries (DLLs) and ActiveX controls. DLLs are shared libraries that contain code and data that multiple programs can use simultaneously. ActiveX controls are software components that allow web browsers and other applications to interact with and display multimedia content.
- The primary purpose of Regsvr32.exe is to register DLLs and ActiveX controls with the Windows Registry. When a DLL or ActiveX control is registered, it means that the operating system is made aware of its existence and its associated functionality. This allows applications to locate and use the registered components when needed.
- It's important to note that the use of Regsvr32.exe requires administrative privileges, as modifying the Windows Registry affects the system-wide settings. Improper use or modification of registered DLLs or ActiveX controls can cause issues with applications that rely on them, so caution should be exercised when using Regsvr32.exe.
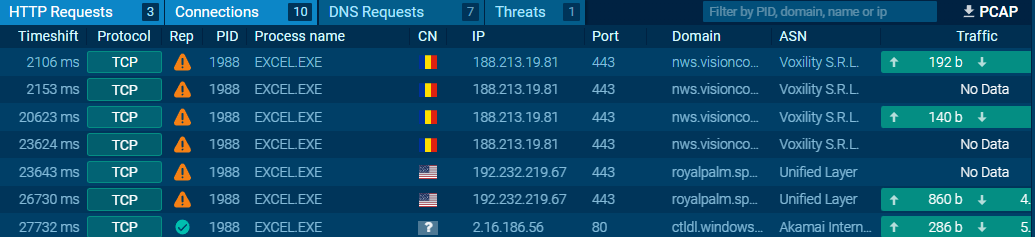
Network Activity
Connections
 |
|---|
| Connections |
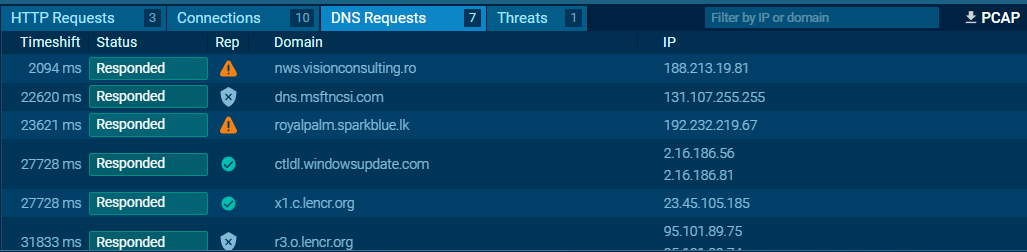
DNS Request
 |
|---|
| DNS Request |
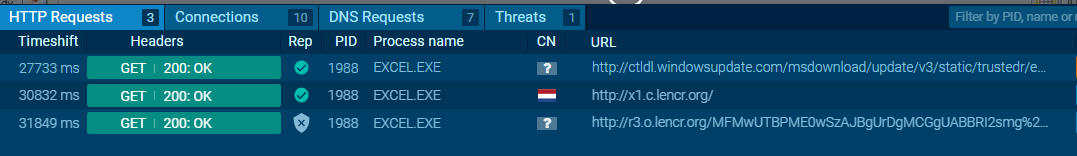
HTTP Requests
 |
|---|
| HTTP Requests |
The malicious excel is trying to communicate with two IPs known to be malicious. and also connected to malicious domains.
Contacted Domains (3)
- nws.visionconsulting.ro
- royalpalm.sparkblue.lk
- ctldl.windowsupdate.com
Contacted IP addresses (3)
- 2.16.186.56:80
- 188.213.19.81:443
- 192.232.219.67:443
Contacted URLs (1)
- http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?cb926953e41013fd
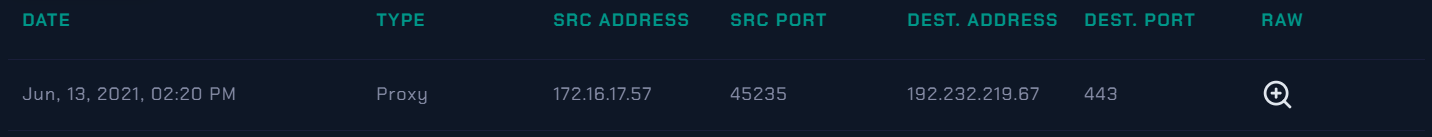
Now Let’s looking for the Log Management.
Now we will use the Log Management page and check if the C2s addresses were accessed 188.213.19.81 - 192.232.219.67
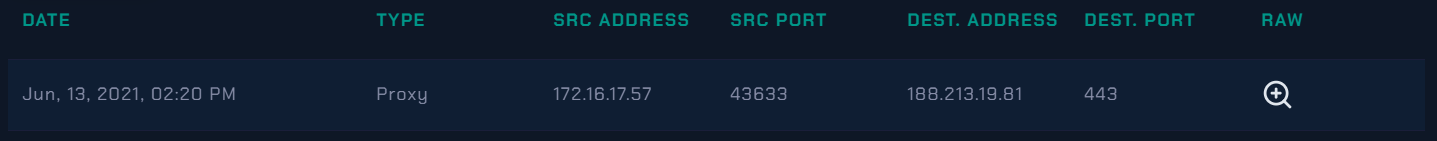 |
|---|
| 188.213.19.81 accessed |
 |
|---|
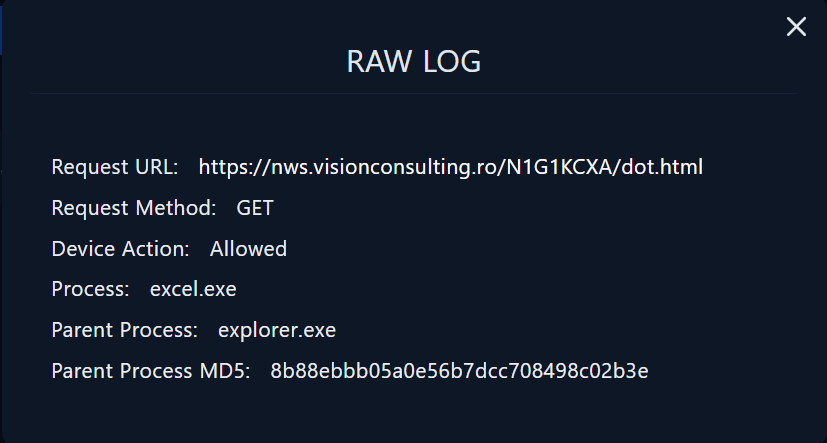
| RAW LOG |
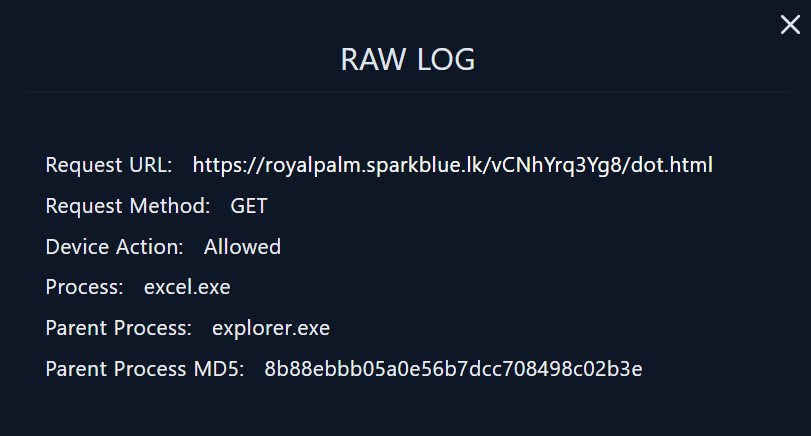
By clicking on the magnifying glass, we can see further details about the raw data. The malicious domain was reached by the user and the action was allowed based on the output.
 |
|---|
| 192.232.219.67 accessed |
 |
|---|
| RAW LOG |
Request URL
- https://royalpalm.sparkblue.lk/vCNhYrq3Yg8/dot.html
- https://nws.visionconsulting.ro/N1G1KCXA/dot.html
Now Let’s looking for the Endpoint Security.
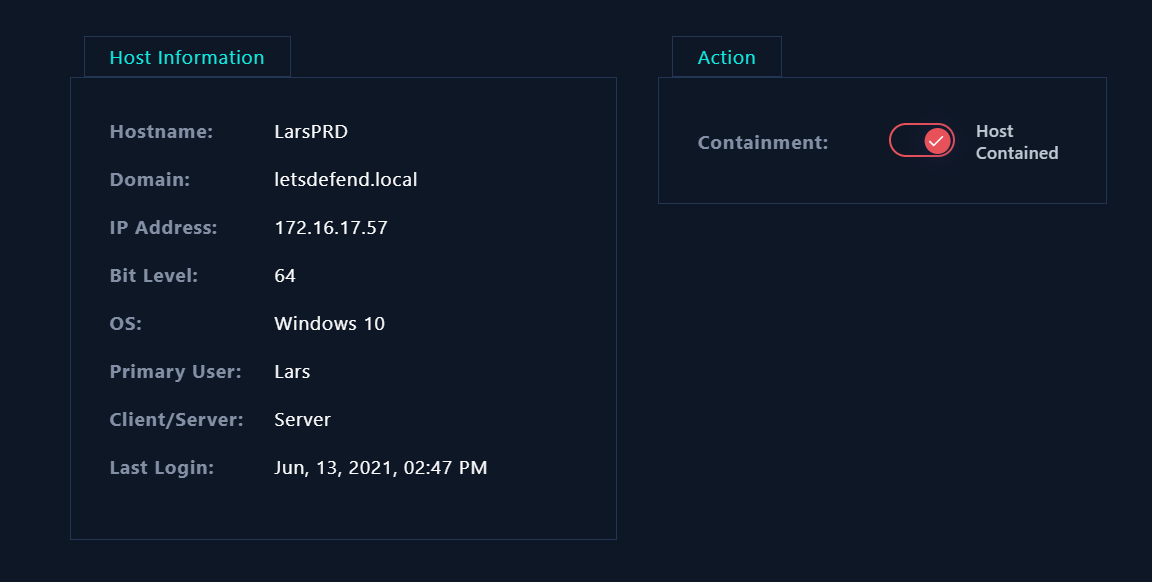
Go to Endpoint Security and Containment the LarsPRD. We can proceed to investigate further for other anomalies on LarsPRD’s workstation.
 |
|---|
| Containment LarsPRD |
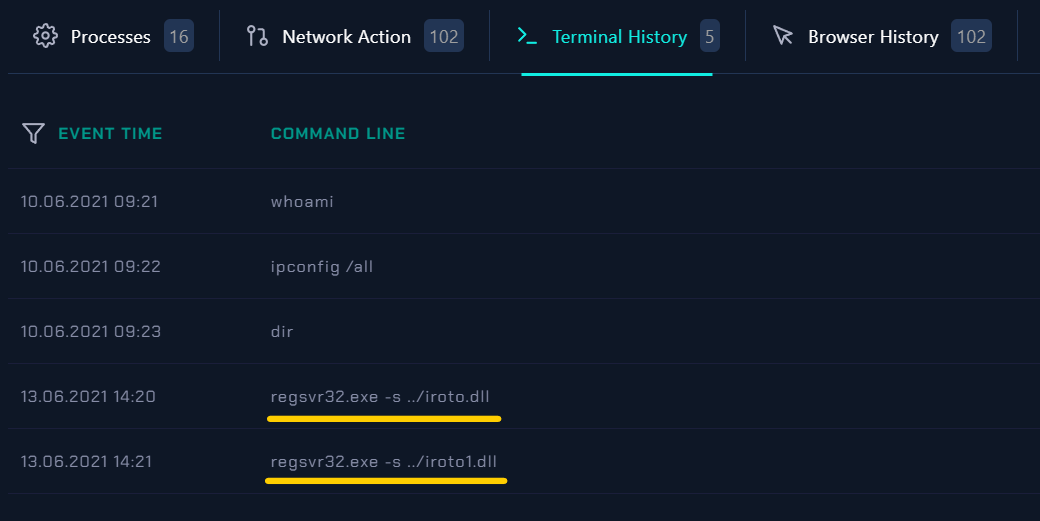
Looking at more details given by the Endpoint Security, we have the option to dig deeper by looking at the Processes, Network Action, Terminal History and Browse History.
 |
|---|
| Terminal History |
In the Terminal History, we can see that the commands:
regsvr32.exe -s ../iroto.dll
regsvr32.exe -s ../iroto1.dll
was executed on the victim machine.
 |
|---|
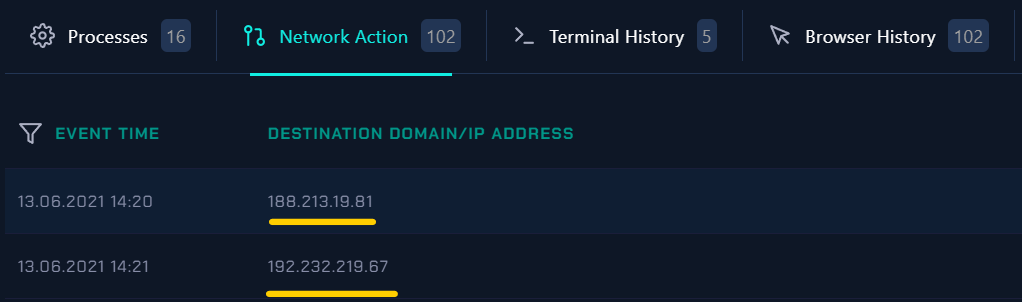
| Network Action |
In the Network Action, we can see that the two malicious IPs were communicating with the victim machine.
 |
|---|
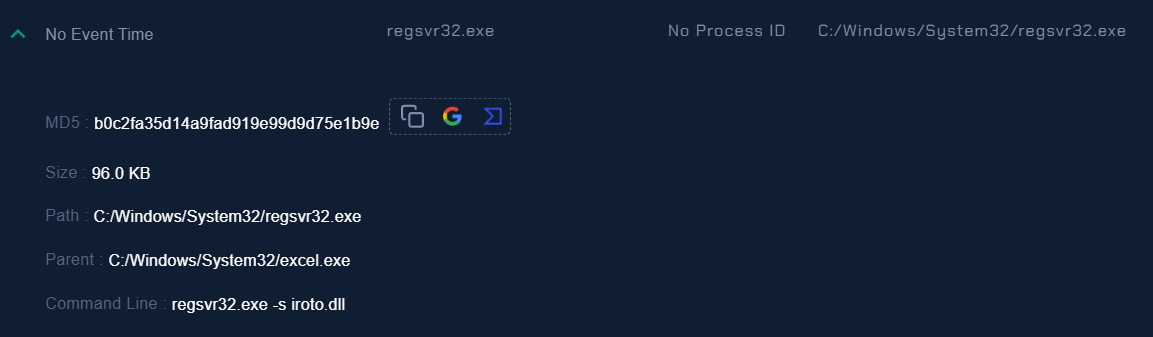
| Processes |
In the Processes, we can see that the process regsvr32.exe was run by the parent process excel.exe and had a command line regsvr32.exe -s iroto.dll.
Case Management
 |
|---|
| Incident Details |
Playbook: A security playbook is a list of required steps and actions needed to successfully respond to any incident or threat. Playbooks provide a step-by-step approach to orchestration, helping security teams to establish standardized incident response processes and ensuring the steps are followed in compliance with regulatory frameworks.
Parse Email
- When was it sent?
- Jun, 13, 2021, 02:11 PM
- What is the email's SMTP address?
- 24.213.228.54
- What is the sender address?
- trenton@tritowncomputers.com
- What is the recipient address?
- lars@letsdefend.io
- Is the mail content suspicious?
- Yes
- Are there any attachment?
- Yes
Are there attachments or URLs in the email?
YesAnalyze Url/Attachment
MaliciousCheck If Mail Delivered to User?
DeliverdCheck If Someone Opened the Malicios File/URL?
Opened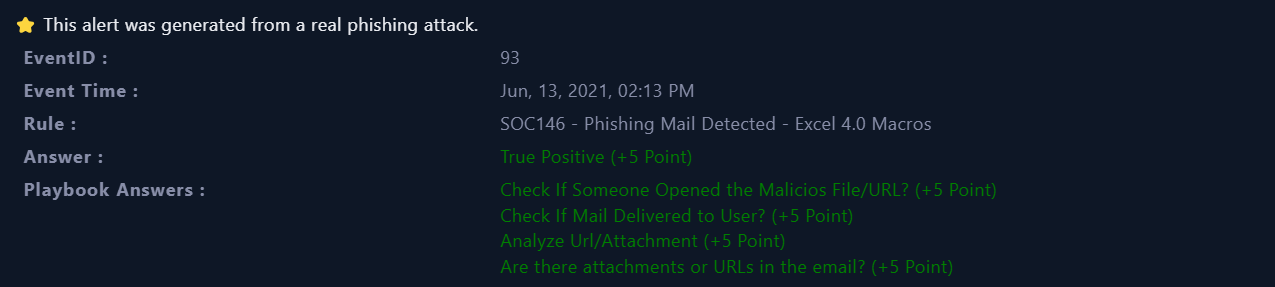 |
|---|
| Playbook Answers |
Protect Your Digital Presence & Stay Cyber Safe 💙
Thanks🌸