Category: SOC - LetsDefend - Ransomware Detected
 |
|---|
| SOC145 - Ransomware Detected |
In this writeup, we will investigate the Ransomware Detected. For those who are not aware of what Ransomware is, this link provides a comprehensive overview of the ransomware.
 |
|---|
| Screenshot For The Alert |
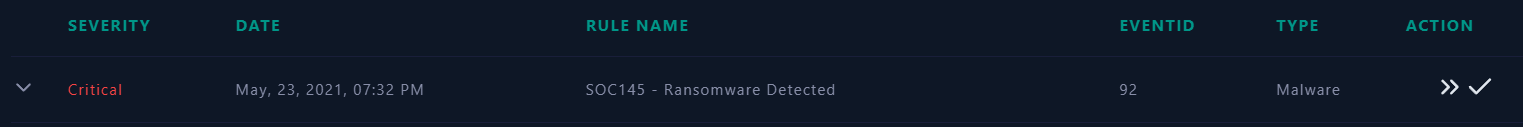
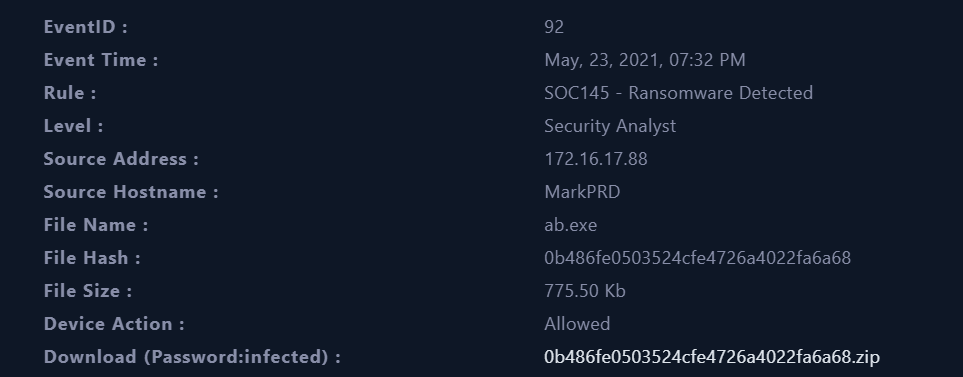
Metadata information of the event which triggered the SIEM alert:
- For this alert, we see that a suspicious behaviour that hit the
SOC145 - Ransomware Detectedrule, we can also see the file name, file hash, and file size.
Let’s get ready to investigate the alert..!
-
For our first step, we can put the hash of the
0b486fe0503524cfe4726a4022fa6a68.zipfile in Virus Total to get a preliminary overview of whether the file is malicious or not and to see if there are any hits returned.File Hash: 1228d0f04f0ba82569fc1c0609f9fd6c377a91b9ea44c1e7f9f84b2b90552da2
Virus Total
 |
|---|
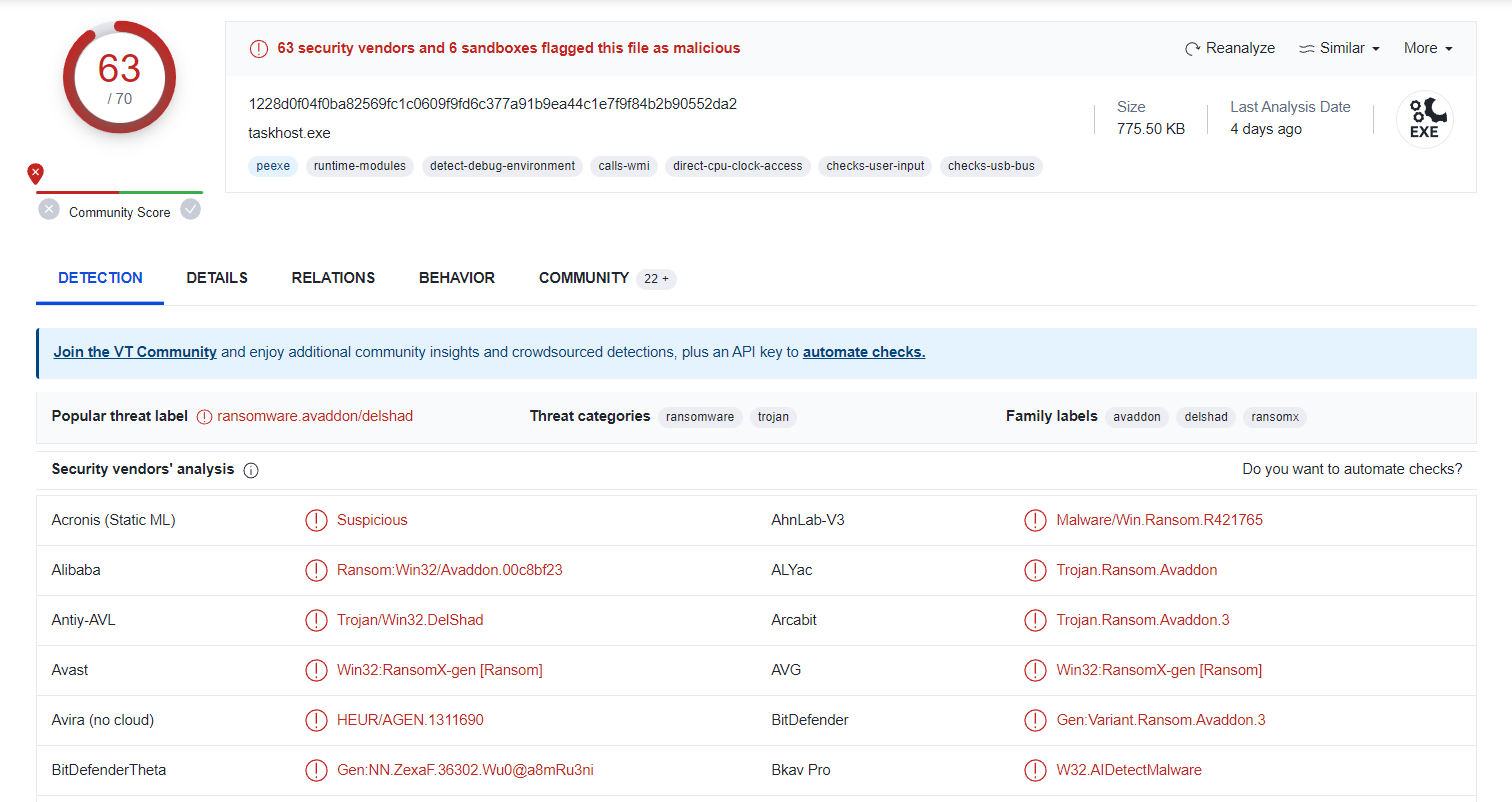
| 0b486fe0503524cfe4726a4022fa6a68.zip seems to be very malicious |
After we submit the file hash in VirusTotal, there are total of 63 security vendors flagged this file as malicious.
 |
|---|
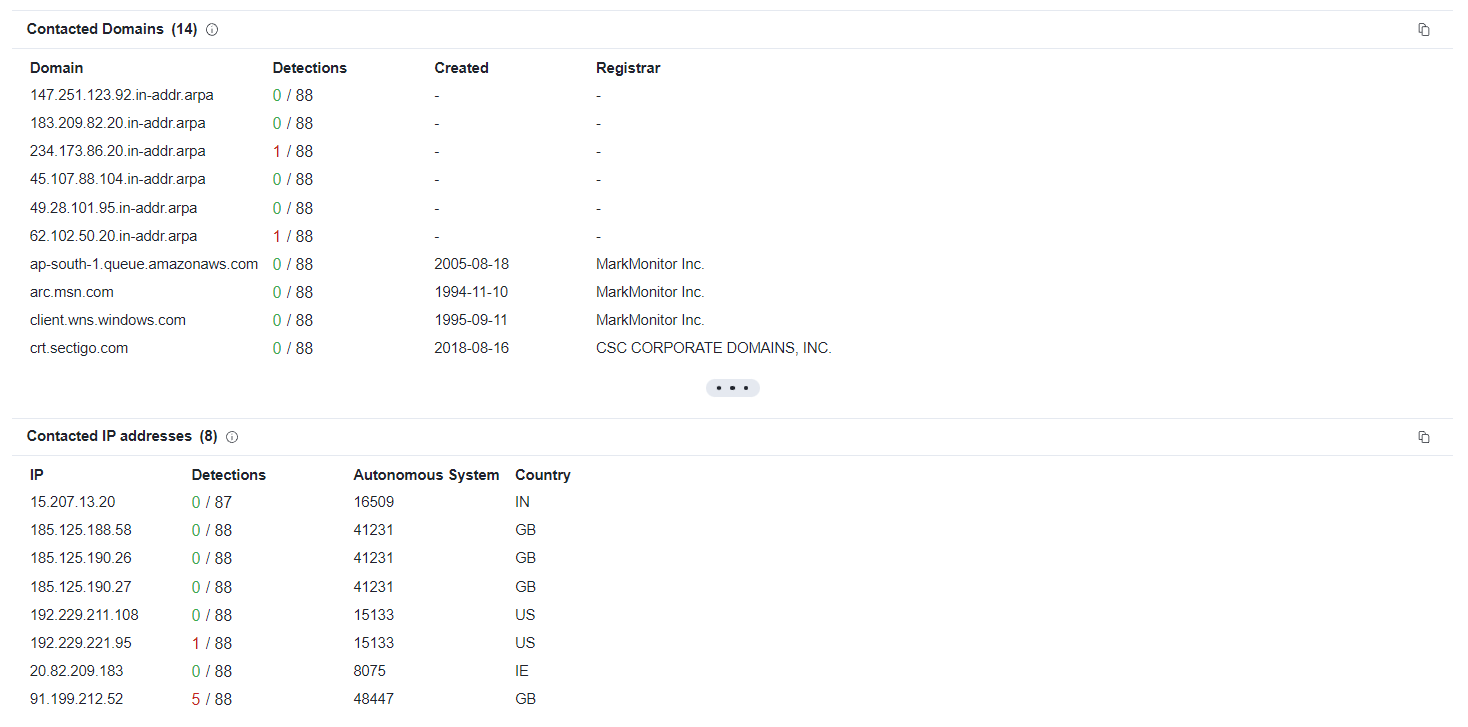
| Relations |
- We can see C2 Adresses, Contacted Domains and URLs relation are also the key indicator for malicious file.
ANY.RUN
Next, we will simulate this artefact’s behaviour on compromised system by submitting it to ANY.RUN
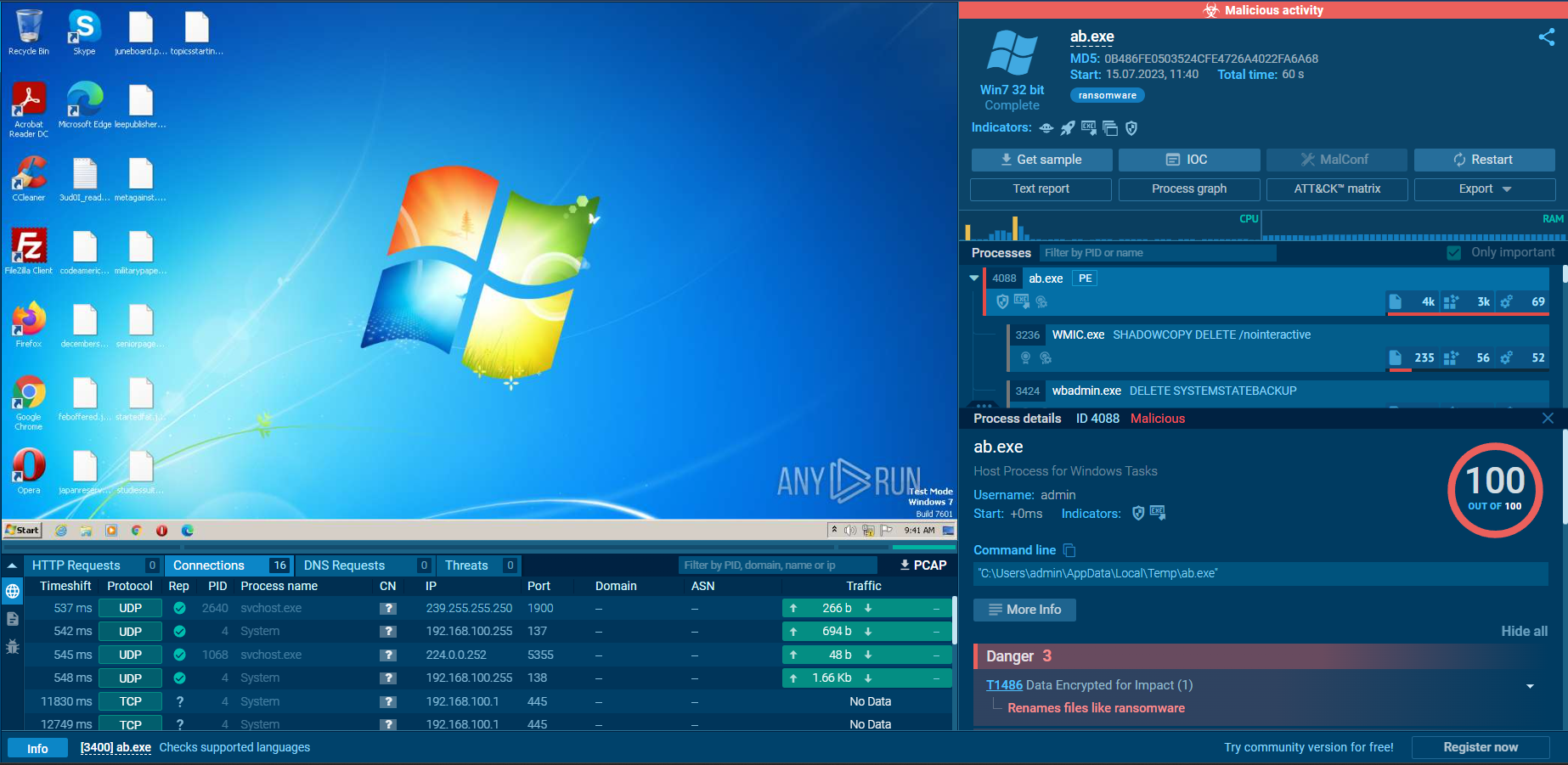 |
|---|
| ANY.RUN |
💡To show more ANY.RUN behaviour analysis result Click Here
Hybrid Analysis
Next, we will simulate this artefact’s behaviour on compromised system by submitting it to Hybrid Analysis
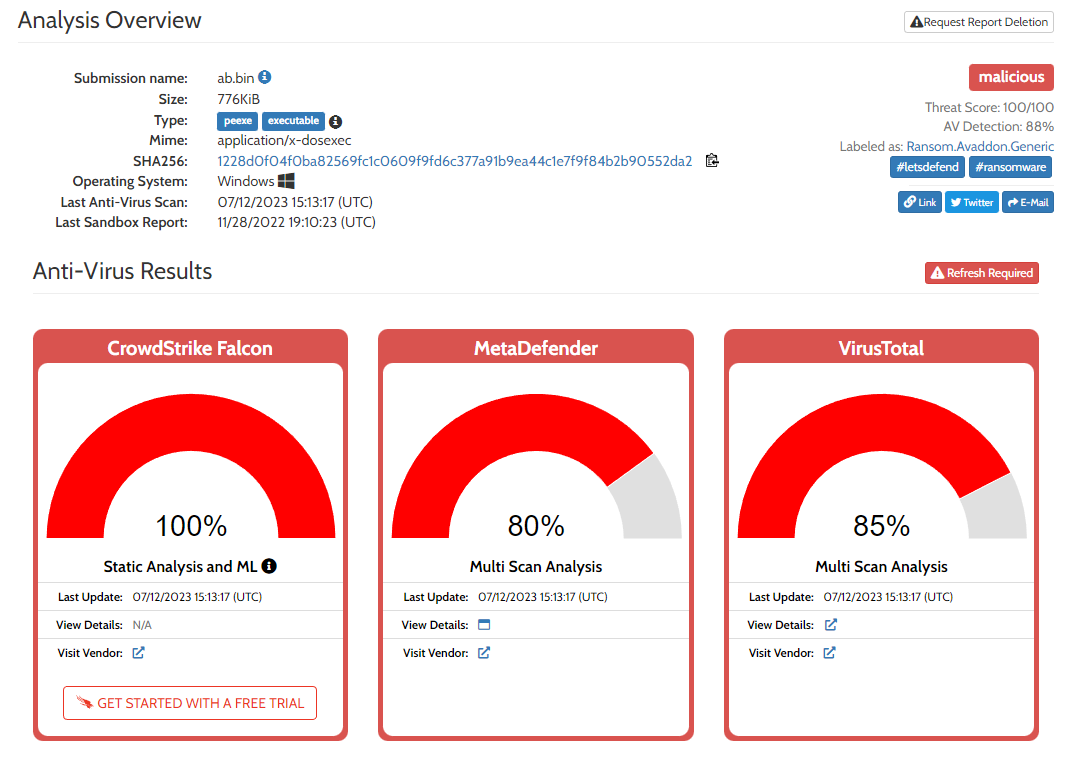 |
|---|
| Hybrid Analysis |
Hybrid Analysis also flagged this file as malicious with detection reference to CrowdStrike Falcon, MetaDefender and VirusTotal.
💡To show more Hybrid Analysis result Click Here
Let’s start with playbook
 |
|---|
| PlayBook |
Define Threat Indicator
 |
|---|
| PlayBook |
Check if the malware is quarantined/cleaned
- First of all you will check Log Management:
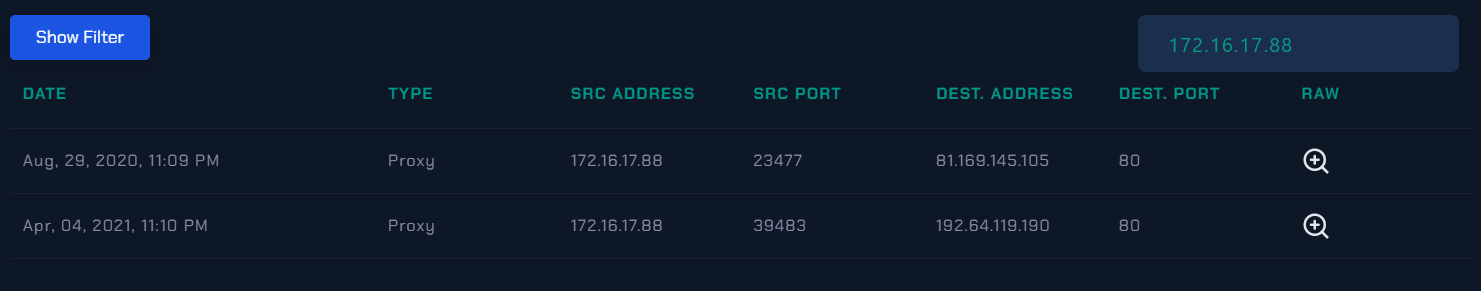 |
|---|
| Log Management |
- First we check the first log alert:
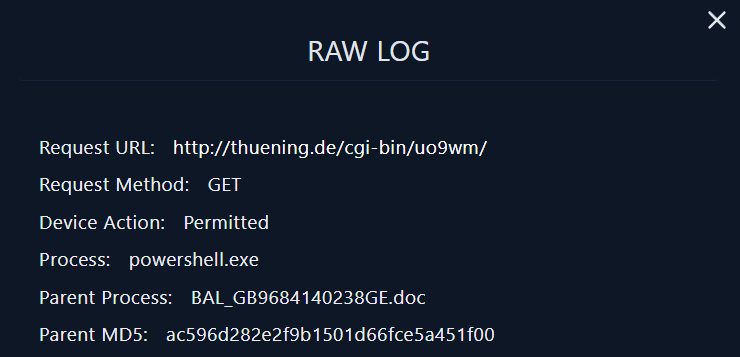 |
|---|
| RAW LOG |
- we check this parent hash in virus total:
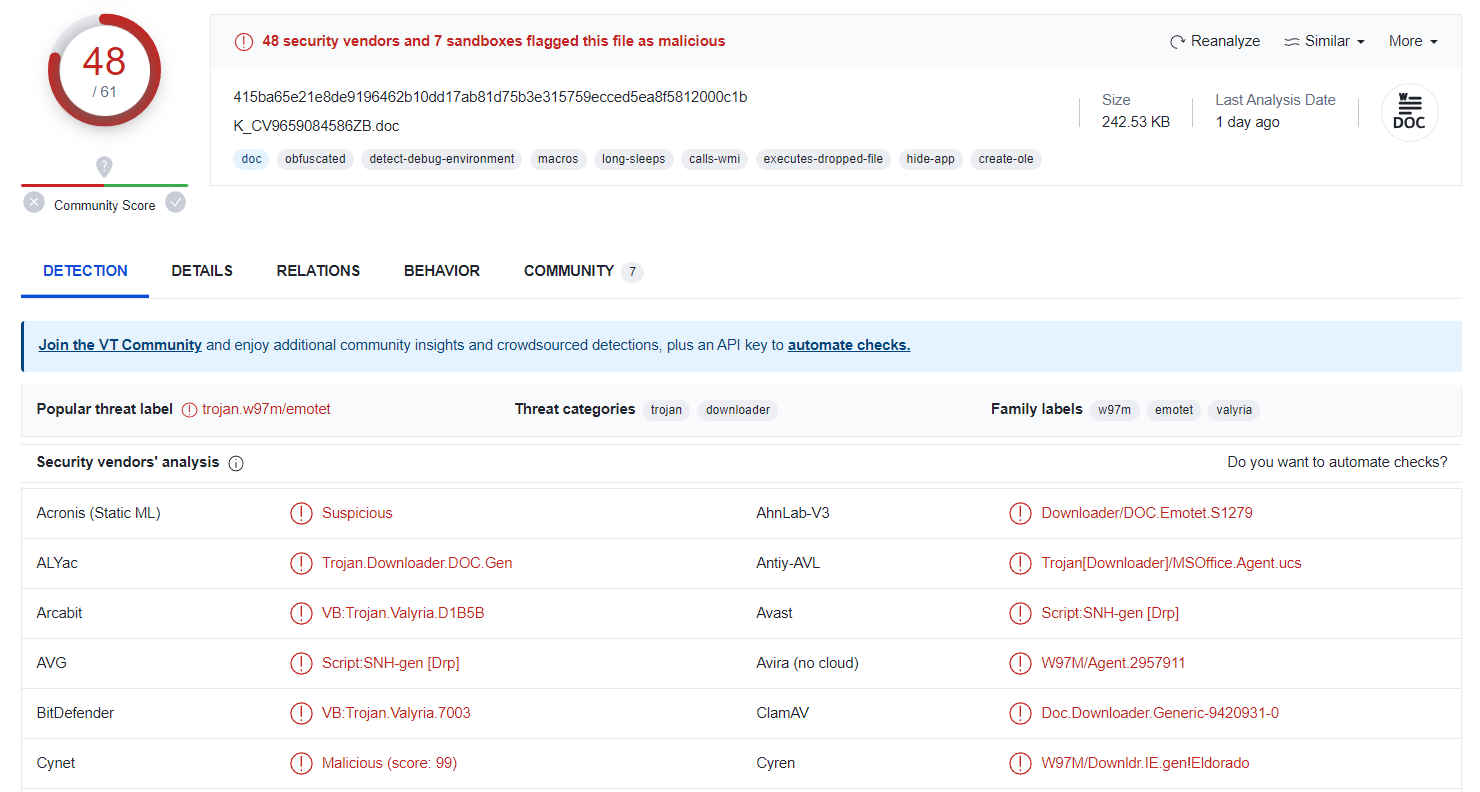 |
After we submit the file hash in VirusTotal, there are total of 48 security vendors flagged this file as malicious.
we will take this information as IoCs:
- Request URL: http://thuening.de/cgi-bin/uo9wm/
- Parent MD5: ac596d282e2f9b1501d66fce5a451f00
- Process: powershell.exe
- Parent Process: BAL_GB9684140238GE.doc
Then we will check the Destination Address:
 |
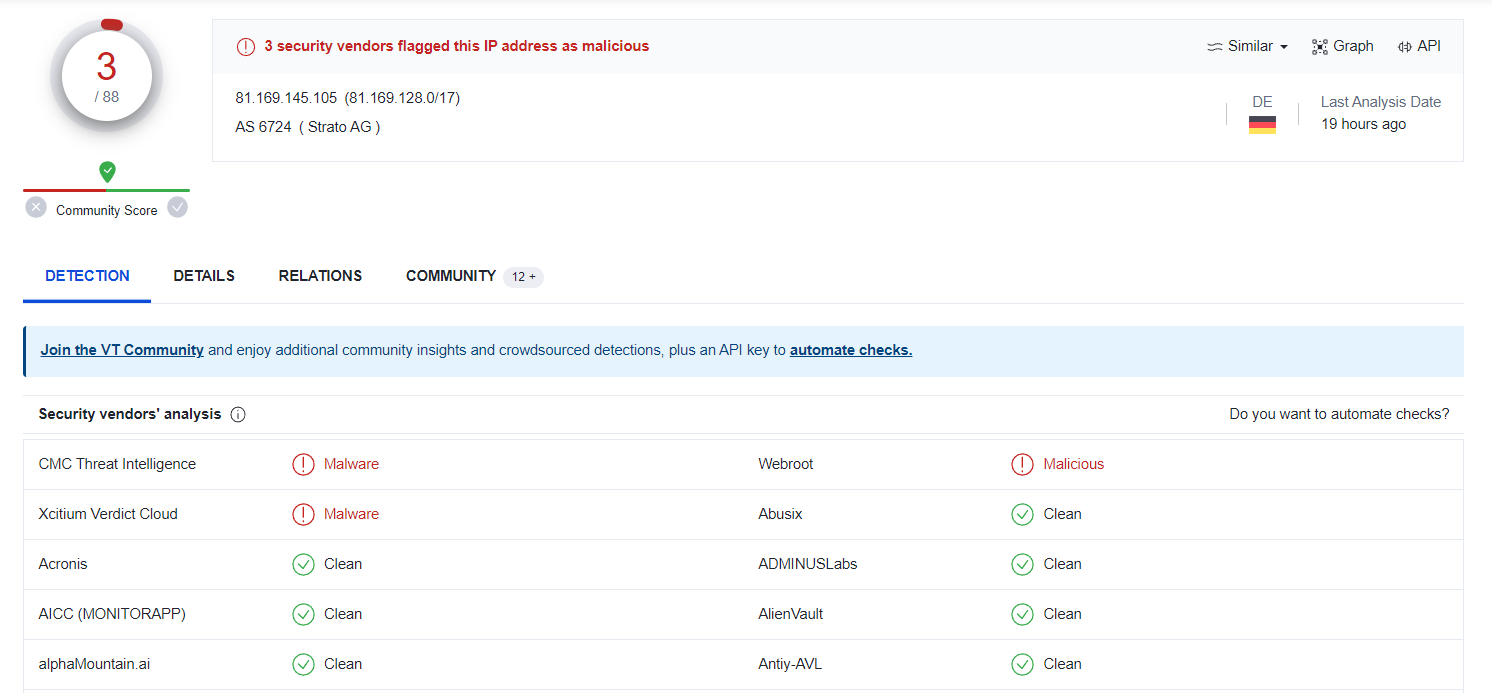
- After we submit the file hash in VirusTotal, there are total of 3 security vendors flagged this IP Address as malicious.
- Now we check the second log alert:
 |
- After we submit the file hash in VirusTotal, there are flagged this file is not malicious.
- Second you will check Endpoint Security:
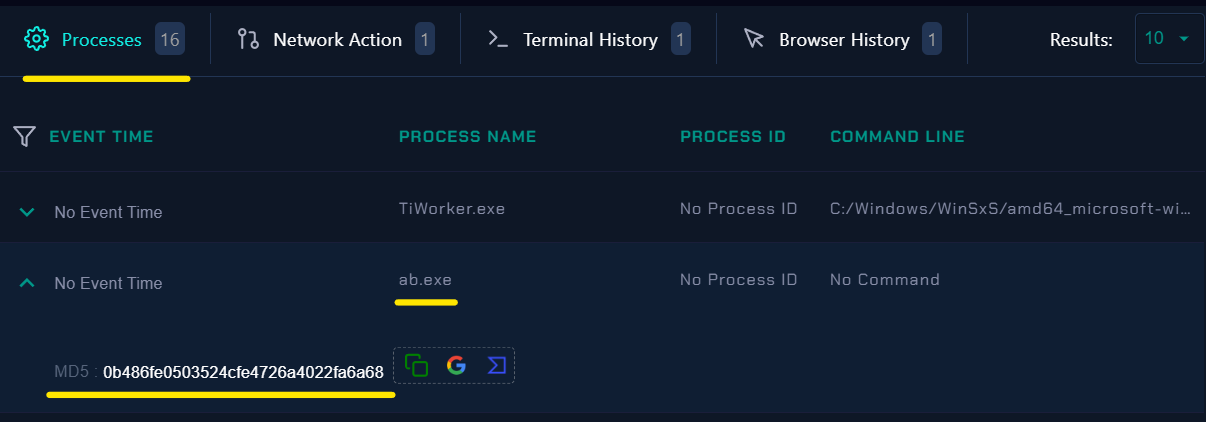 |
|---|
| Endpoint Security |
- If we check this hash
0b486fe0503524cfe4726a4022fa6a68in virus total:
 |
|---|
| Virus Total |
And this is basic properties and names of this file:
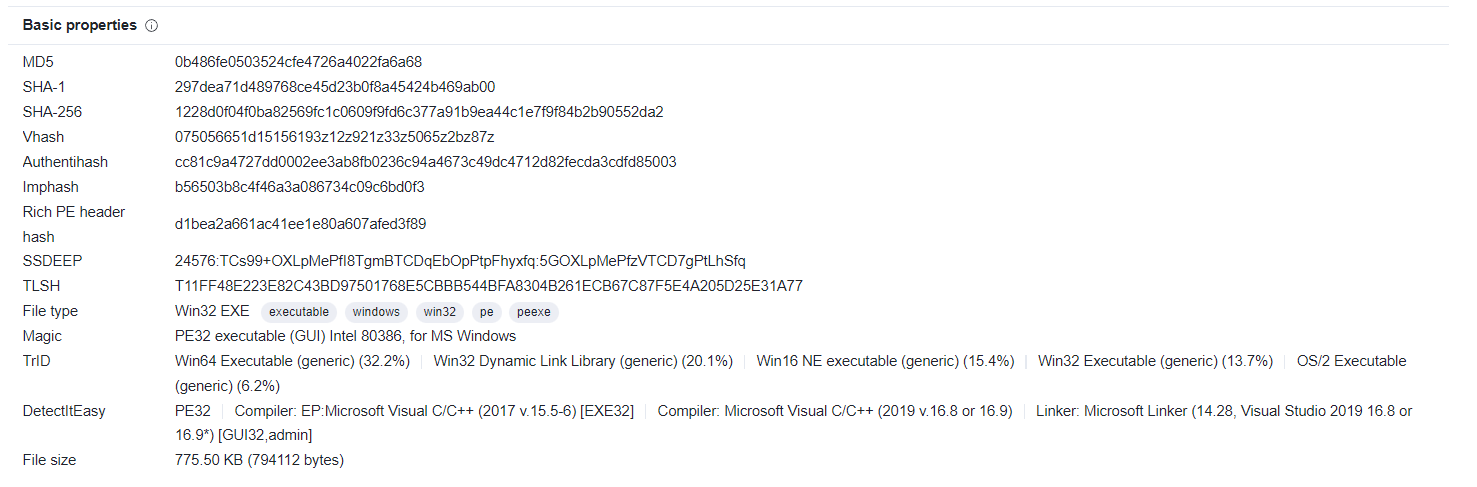 |
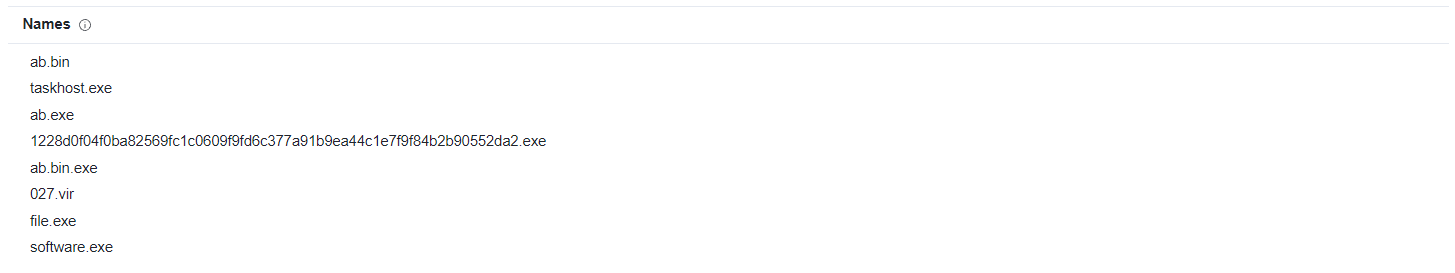 |
💡To show more details about this file Click Here and for relations Click Here
Finally,
It is True Positive alert, because ab.exe is ransomware and encrypted all files on the machine. There is no C2 address, if you do dynamic analysis, you can see how it is acting.
Protect Your Digital Presence & Stay Cyber Safe 💙
Thanks🌸